 -Route 53 is a Domain Name System (DNS) service that performs global server load balancing by routing each request to the AWS region closest to the requester's location. This guide uses two regions: **US West (Oregon)** and **US East (N. Virginia)**.
+Route 53 is a Domain Name System (DNS) service that performs global server load balancing by routing each request to the AWS region closest to the requester's location. This guide uses two regions: {{
-Route 53 is a Domain Name System (DNS) service that performs global server load balancing by routing each request to the AWS region closest to the requester's location. This guide uses two regions: **US West (Oregon)** and **US East (N. Virginia)**.
+Route 53 is a Domain Name System (DNS) service that performs global server load balancing by routing each request to the AWS region closest to the requester's location. This guide uses two regions: {{ @@ -87,7 +87,7 @@ Create a _hosted zone_, which basically involves designating a domain name to be
@@ -87,7 +87,7 @@ Create a _hosted zone_, which basically involves designating a domain name to be
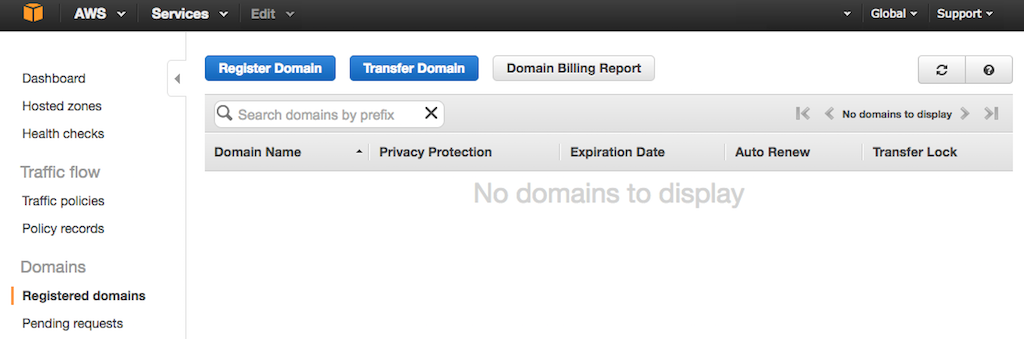 - If you see the Route 53 home page instead, access the **Registered domains** tab by clicking the Get started now button under **Domain registration**.
+ If you see the Route 53 home page instead, access the **Registered domains** tab by clicking the Get started now button under {{
- If you see the Route 53 home page instead, access the **Registered domains** tab by clicking the Get started now button under **Domain registration**.
+ If you see the Route 53 home page instead, access the **Registered domains** tab by clicking the Get started now button under {{ @@ -124,19 +124,19 @@ Create records sets for your domain:
4. Fill in the fields in the **Create Record Set** column:
- **Name** – You can leave this field blank, but for this guide we are setting the name to **www.nginxroute53.com**.
- - **Type** – **A – IPv4 address**.
+ - **Type** – **A {{
@@ -124,19 +124,19 @@ Create records sets for your domain:
4. Fill in the fields in the **Create Record Set** column:
- **Name** – You can leave this field blank, but for this guide we are setting the name to **www.nginxroute53.com**.
- - **Type** – **A – IPv4 address**.
+ - **Type** – **A {{ -2. Click the Create health check button. In the **Configure health check** form that opens, specify the following values, then click the Next button.
+2. Click the Create health check button. In the {{
-2. Click the Create health check button. In the **Configure health check** form that opens, specify the following values, then click the Next button.
+2. Click the Create health check button. In the {{ -3. On the **Get notified when health check fails** screen that opens, set the **Create alarm** radio button to **Yes** or **No** as appropriate, then click the Create health check button.
+3. On the {{
-3. On the **Get notified when health check fails** screen that opens, set the **Create alarm** radio button to **Yes** or **No** as appropriate, then click the Create health check button.
+3. On the {{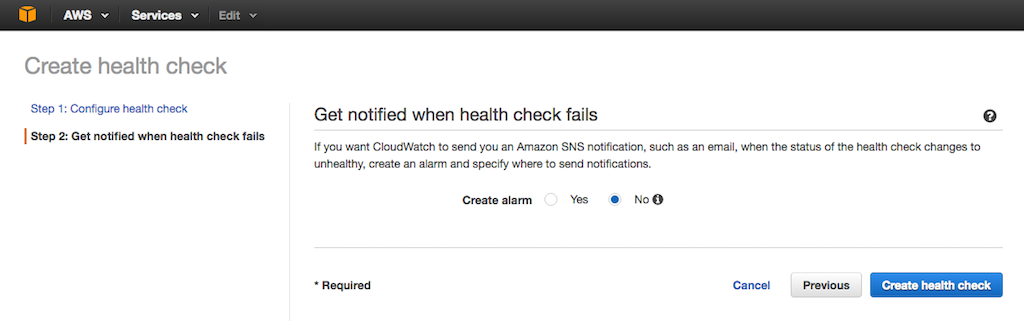 -4. Repeat Steps 2 and 3 for your other NGINX Plus load balancers (in this guide, **US West LB 2**, **US East LB 1**, and **US East LB 2**).
+4. Repeat Steps 2 and 3 for your other NGINX Plus load balancers (in this guide, {{
-4. Repeat Steps 2 and 3 for your other NGINX Plus load balancers (in this guide, **US West LB 2**, **US East LB 1**, and **US East LB 2**).
+4. Repeat Steps 2 and 3 for your other NGINX Plus load balancers (in this guide, {{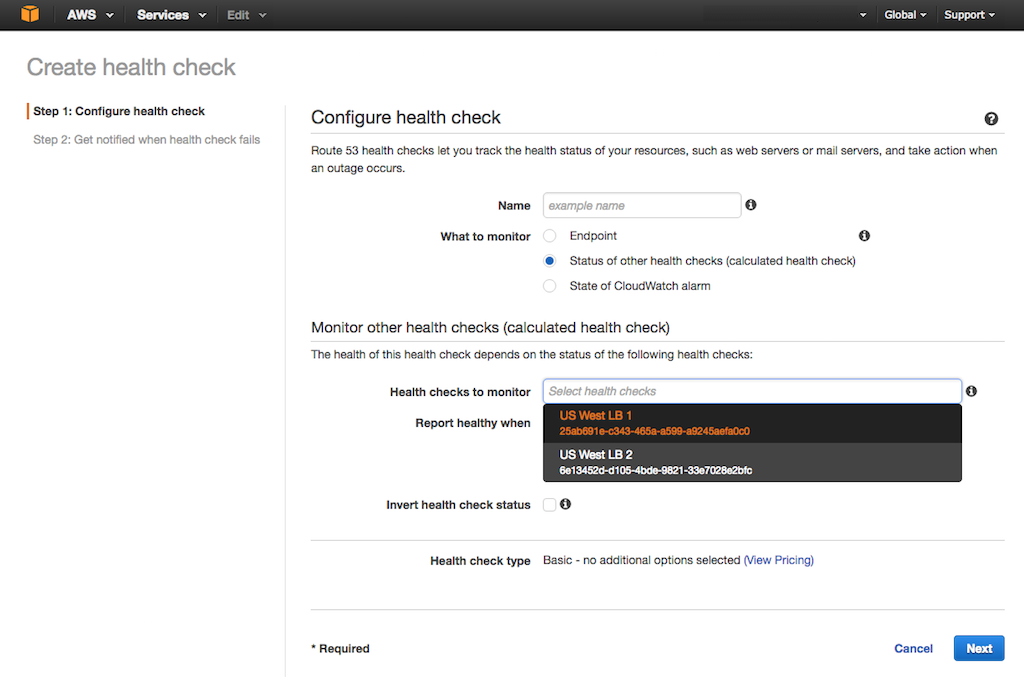 -3. On the **Get notified when health check fails** screen that opens, set the **Create alarm** radio button as appropriate (see Step 5 in the previous section), then click the Create health check button.
+3. On the {{
-3. On the **Get notified when health check fails** screen that opens, set the **Create alarm** radio button as appropriate (see Step 5 in the previous section), then click the Create health check button.
+3. On the {{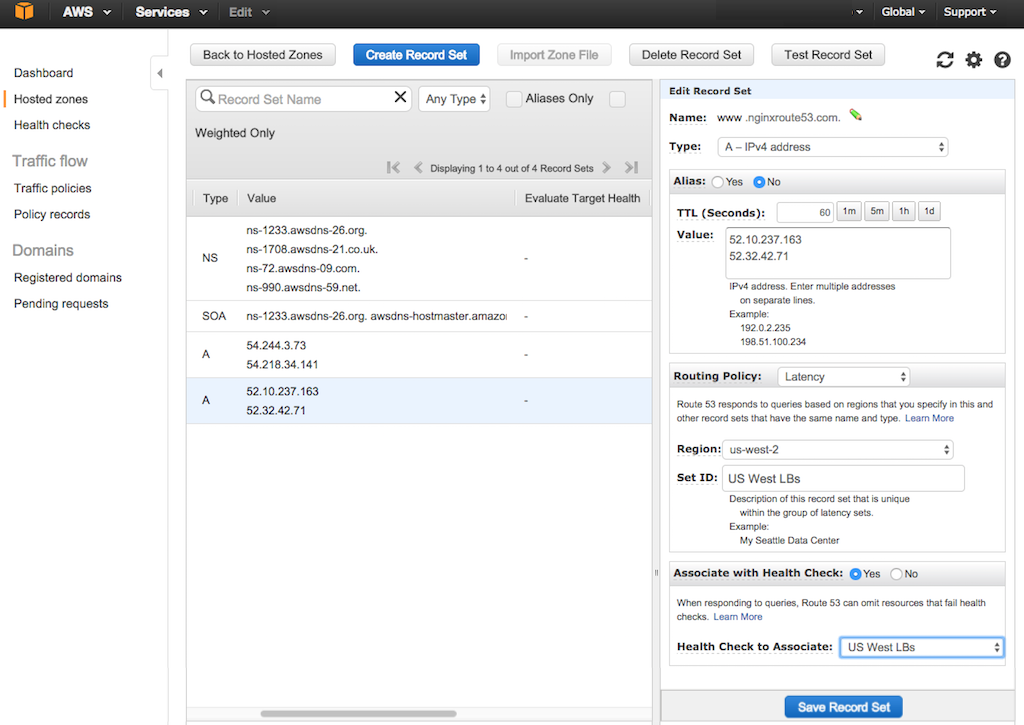 4. Change the **Associate with Health Check** radio button to **Yes**.
-5. In the **Health Check to Associate** field, select the paired health check for your first region (in this guide, **US West LBs**).
+5. In the **Health Check to Associate** field, select the paired health check for your first region (in this guide, {{
4. Change the **Associate with Health Check** radio button to **Yes**.
-5. In the **Health Check to Associate** field, select the paired health check for your first region (in this guide, **US West LBs**).
+5. In the **Health Check to Associate** field, select the paired health check for your first region (in this guide, {{ @@ -366,7 +366,7 @@ After you complete the instructions on all instances, the list for a region (her
### Configuring NGINX Open Source on the Backend Servers
-Perform these steps on all four backend servers: **Backend 1**, **Backend 2**, **Backend 3**, and **Backend 4**. In Step 3, substitute the appropriate name for `Backend X` in the **index.html** file.
+Perform these steps on all four backend servers: {{
@@ -366,7 +366,7 @@ After you complete the instructions on all instances, the list for a region (her
### Configuring NGINX Open Source on the Backend Servers
-Perform these steps on all four backend servers: **Backend 1**, **Backend 2**, **Backend 3**, and **Backend 4**. In Step 3, substitute the appropriate name for `Backend X` in the **index.html** file.
+Perform these steps on all four backend servers: {{ -3. The **Shed Load** filter is added as the fourth (lowest) box in the **Active Filters** section. Move it to be third by clicking and dragging it above the **Select First N** box.
+3. The **Shed Load** filter is added as the fourth (lowest) box in the **Active Filters** section. Move it to be third by clicking and dragging it above the {{
-3. The **Shed Load** filter is added as the fourth (lowest) box in the **Active Filters** section. Move it to be third by clicking and dragging it above the **Select First N** box.
+3. The **Shed Load** filter is added as the fourth (lowest) box in the **Active Filters** section. Move it to be third by clicking and dragging it above the {{ - - If there are existing projects, the name of one of them appears in the upper left of the blue header bar (in the screenshot, it's My Test Project ). Click the project name and select **Create project** from the menu that opens.
+ - If there are existing projects, the name of one of them appears in the upper left of the blue header bar (in the screenshot, it's My Test Project ). Click the project name and select {{
- - If there are existing projects, the name of one of them appears in the upper left of the blue header bar (in the screenshot, it's My Test Project ). Click the project name and select **Create project** from the menu that opens.
+ - If there are existing projects, the name of one of them appears in the upper left of the blue header bar (in the screenshot, it's My Test Project ). Click the project name and select {{ -3. Type your project name in the **New Project** window that pops up, then click CREATE. We're naming the project **NGINX Plus All‑Active‑LB**.
+3. Type your project name in the {{
-3. Type your project name in the **New Project** window that pops up, then click CREATE. We're naming the project **NGINX Plus All‑Active‑LB**.
+3. Type your project name in the {{ @@ -87,24 +87,24 @@ Create a new GCE project to host the all‑active NGINX Plus deployment.
Create firewall rules that allow access to the HTTP and HTTPS ports on your GCE instances. You'll attach the rules to all the instances you create for the deployment.
-1. Navigate to the **Networking > Firewall rules** tab and click + CREATE FIREWALL RULE. (The screenshot shows the default rules provided by GCE.)
+1. Navigate to the {{
@@ -87,24 +87,24 @@ Create a new GCE project to host the all‑active NGINX Plus deployment.
Create firewall rules that allow access to the HTTP and HTTPS ports on your GCE instances. You'll attach the rules to all the instances you create for the deployment.
-1. Navigate to the **Networking > Firewall rules** tab and click + CREATE FIREWALL RULE. (The screenshot shows the default rules provided by GCE.)
+1. Navigate to the {{ -2. Fill in the fields on the **Create a firewall rule** screen that opens:
+2. Fill in the fields on the {{
-2. Fill in the fields on the **Create a firewall rule** screen that opens:
+2. Fill in the fields on the {{ -3. Click the Create button. The new rule is added to the table on the **Firewall rules** tab.
+3. Click the Create button. The new rule is added to the table on the {{
-3. Click the Create button. The new rule is added to the table on the **Firewall rules** tab.
+3. Click the Create button. The new rule is added to the table on the {{ - - **Identity and API access** – Keep the defaults for the **Service account ** field and **Access scopes** radio button. Unless you need more granular control.
+ - {{
- - **Identity and API access** – Keep the defaults for the **Service account ** field and **Access scopes** radio button. Unless you need more granular control.
+ - {{ @@ -166,38 +166,38 @@ Create three source VM instances based on a GCE VM image. We're basing our insta
@@ -166,38 +166,38 @@ Create three source VM instances based on a GCE VM image. We're basing our insta
 -5. On the **Networking** subtab, verify the default settings, in particular **Ephemeral** for **External IP** and **Off** for **IP Forwarding**.
+5. On the **Networking** subtab, verify the default settings, in particular **Ephemeral** for {{
-5. On the **Networking** subtab, verify the default settings, in particular **Ephemeral** for **External IP** and **Off** for **IP Forwarding**.
+5. On the **Networking** subtab, verify the default settings, in particular **Ephemeral** for {{ -6. If you're using your own SSH public key instead of your default GCE keys, paste the hexadecimal key string on the **SSH Keys** subtab. Right into the box that reads **Enter entire key data**.
+6. If you're using your own SSH public key instead of your default GCE keys, paste the hexadecimal key string on the {{
-6. If you're using your own SSH public key instead of your default GCE keys, paste the hexadecimal key string on the **SSH Keys** subtab. Right into the box that reads **Enter entire key data**.
+6. If you're using your own SSH public key instead of your default GCE keys, paste the hexadecimal key string on the {{ -7. Click the Create button at the bottom of the **Create an instance** page.
+7. Click the Create button at the bottom of the {{
-7. Click the Create button at the bottom of the **Create an instance** page.
+7. Click the Create button at the bottom of the {{ #### Creating the Second Application Instance from a VM Image
-1. On the **VM instances** summary page, click CREATE INSTANCE.
+1. On the {{
#### Creating the Second Application Instance from a VM Image
-1. On the **VM instances** summary page, click CREATE INSTANCE.
+1. On the {{ @@ -253,7 +253,7 @@ Now install NGINX Plus and download files that are specific to the all‑active
Both the configuration and content files are available at the [NGINX GitHub repository](https://github.com/nginxinc/NGINX-Demos/tree/master/gce-nginx-plus-deployment-guide-files).
-Repeat these instructions for all three source instances (**nginx‑plus‑app‑1**, **nginx‑plus‑app‑2**, and **nginx‑plus‑lb**).
+Repeat these instructions for all three source instances ({{
@@ -253,7 +253,7 @@ Now install NGINX Plus and download files that are specific to the all‑active
Both the configuration and content files are available at the [NGINX GitHub repository](https://github.com/nginxinc/NGINX-Demos/tree/master/gce-nginx-plus-deployment-guide-files).
-Repeat these instructions for all three source instances (**nginx‑plus‑app‑1**, **nginx‑plus‑app‑2**, and **nginx‑plus‑lb**).
+Repeat these instructions for all three source instances ({{ @@ -392,25 +392,25 @@ Create three source instances based on a prebuilt NGINX Plus image running on <
@@ -392,25 +392,25 @@ Create three source instances based on a prebuilt NGINX Plus image running on <
 -7. Navigate to the **Compute Engine > VM instances** tab and click **nginx‑plus‑app‑1‑vm** in the Name column in the table. (The **‑vm** suffix is added automatically to the name of the newly created instance.)
+7. Navigate to the {{
-7. Navigate to the **Compute Engine > VM instances** tab and click **nginx‑plus‑app‑1‑vm** in the Name column in the table. (The **‑vm** suffix is added automatically to the name of the newly created instance.)
+7. Navigate to the {{ -8. On the **VM instances** page that opens, click EDIT at the top of the page. In fields that can be edited, the value changes from static text to text boxes, drop‑down menus, and checkboxes.
+8. On the {{
-8. On the **VM instances** page that opens, click EDIT at the top of the page. In fields that can be edited, the value changes from static text to text boxes, drop‑down menus, and checkboxes.
+8. On the {{ -2. Click **nginx‑plus‑app‑1‑vm** in the Name column of the table (shown in the screenshot in Step 7 of Creating the First Application Instance).
+2. Click {{
-2. Click **nginx‑plus‑app‑1‑vm** in the Name column of the table (shown in the screenshot in Step 7 of Creating the First Application Instance).
+2. Click {{ - - On the **VM instances** page that opens, click EDIT at the top of the page. In fields that can be edited, the value changes from static text to text boxes, drop‑down menus, and checkboxes.
- - In the **Boot disk and local disks** field, uncheck the checkbox labeled **Delete boot disk when instance is deleted**.
+ - On the {{
- - On the **VM instances** page that opens, click EDIT at the top of the page. In fields that can be edited, the value changes from static text to text boxes, drop‑down menus, and checkboxes.
- - In the **Boot disk and local disks** field, uncheck the checkbox labeled **Delete boot disk when instance is deleted**.
+ - On the {{ - - Select **NGINX Plus All‑Active‑LB** from the drop-down menu labeled **Show images from**.
+ - Select **NGINX {{
- - Select **NGINX Plus All‑Active‑LB** from the drop-down menu labeled **Show images from**.
+ - Select **NGINX {{ @@ -728,11 +728,11 @@ Create _instance templates_. They are the compute workloads in instance groups.
@@ -728,11 +728,11 @@ Create _instance templates_. They are the compute workloads in instance groups.
 -8. On the **Networking** subtab, verify the default settings of **Ephemeral** for **External IP** and **Off** for **IP Forwarding**.
+8. On the **Networking** subtab, verify the default settings of **Ephemeral** for {{
-8. On the **Networking** subtab, verify the default settings of **Ephemeral** for **External IP** and **Off** for **IP Forwarding**.
+8. On the **Networking** subtab, verify the default settings of **Ephemeral** for {{ -9. If you're using your own SSH public key instead of your default keys, paste the hexadecimal key string on the **SSH Keys** subtab. Right into the box that reads **Enter entire key data**.
+9. If you're using your own SSH public key instead of your default keys, paste the hexadecimal key string on the {{
-9. If you're using your own SSH public key instead of your default keys, paste the hexadecimal key string on the **SSH Keys** subtab. Right into the box that reads **Enter entire key data**.
+9. If you're using your own SSH public key instead of your default keys, paste the hexadecimal key string on the {{ @@ -741,25 +741,25 @@ Create _instance templates_. They are the compute workloads in instance groups.
### Creating the Second Application Instance Template
-1. On the **Instance templates** summary page, click CREATE INSTANCE TEMPLATE.
+1. On the {{
@@ -741,25 +741,25 @@ Create _instance templates_. They are the compute workloads in instance groups.
### Creating the Second Application Instance Template
-1. On the **Instance templates** summary page, click CREATE INSTANCE TEMPLATE.
+1. On the {{ -6. Navigate to the **Networking > Load balancing** tab.
+6. Navigate to the {{
-6. Navigate to the **Networking > Load balancing** tab.
+6. Navigate to the {{ -13. Select **Frontend configuration** in the left column. This opens up the **Frontend configuration** interface on the right column.
+13. Select {{
-13. Select **Frontend configuration** in the left column. This opens up the **Frontend configuration** interface on the right column.
+13. Select {{ -4. On the **lb | Backend Pools** page that opens, click **+ Add** in the upper left corner of the main pane.
+4. On the {{
-4. On the **lb | Backend Pools** page that opens, click **+ Add** in the upper left corner of the main pane.
+4. On the {{ After a few moments the virtual machines appear in the new backend pool.
-6. Click **Health probes** in the left navigation column, and then **+ Add** in the upper left corner of the main pane on the **lb | Health probes** page that opens.
+6. Click **Health probes** in the left navigation column, and then **+ Add** in the upper left corner of the main pane on the {{
After a few moments the virtual machines appear in the new backend pool.
-6. Click **Health probes** in the left navigation column, and then **+ Add** in the upper left corner of the main pane on the **lb | Health probes** page that opens.
+6. Click **Health probes** in the left navigation column, and then **+ Add** in the upper left corner of the main pane on the {{ - After a few moments the new probe appears in the table on the **lb | Health probes** page. This probe queries the NGINX Plus landing page every five seconds to check whether NGINX Plus is running.
+ After a few moments the new probe appears in the table on the {{
- After a few moments the new probe appears in the table on the **lb | Health probes** page. This probe queries the NGINX Plus landing page every five seconds to check whether NGINX Plus is running.
+ After a few moments the new probe appears in the table on the {{ - After a few moments the new rule appears in the table on the **lb | Load balancing rules** page.
+ After a few moments the new rule appears in the table on the {{
- After a few moments the new rule appears in the table on the **lb | Load balancing rules** page.
+ After a few moments the new rule appears in the table on the {{ @@ -210,7 +210,7 @@ Once you’ve tested that the Standard Load Balancer has been correctly deployed
In this case, you need to set up Azure Traffic Manager for DNS‑based global server load balancing (GSLB) among the regions. The involves creating a DNS name for the Standard Load Balancer and registering it as an endpoint in Traffic Manager.
-1. Navigate to the **Public IP addresses** page. (One way is to enter **Public IP addresses** in the search field of the Azure title bar and select that value in the **Services** section of the resulting drop‑down menu.)
+1. Navigate to the {{
@@ -210,7 +210,7 @@ Once you’ve tested that the Standard Load Balancer has been correctly deployed
In this case, you need to set up Azure Traffic Manager for DNS‑based global server load balancing (GSLB) among the regions. The involves creating a DNS name for the Standard Load Balancer and registering it as an endpoint in Traffic Manager.
-1. Navigate to the **Public IP addresses** page. (One way is to enter **Public IP addresses** in the search field of the Azure title bar and select that value in the **Services** section of the resulting drop‑down menu.)
+1. Navigate to the {{ -5. Navigate to the **Traffic Manager profiles** tab. (One way is to enter **Traffic Manager profiles** in the search field of the Azure title bar and select that value in the **Services** section of the resulting drop‑down menu.)
+5. Navigate to the {{
-5. Navigate to the **Traffic Manager profiles** tab. (One way is to enter **Traffic Manager profiles** in the search field of the Azure title bar and select that value in the **Services** section of the resulting drop‑down menu.)
+5. Navigate to the {{ -8. It takes a few moments to create the profile. When it appears in the table on the **Traffic Manager profiles** page, click its name in the **Name** column.
+8. It takes a few moments to create the profile. When it appears in the table on the {{
-8. It takes a few moments to create the profile. When it appears in the table on the **Traffic Manager profiles** page, click its name in the **Name** column.
+8. It takes a few moments to create the profile. When it appears in the table on the {{ @@ -75,7 +75,7 @@ In addition, to install NGINX software by following the linked instructions, you
For simplicity, we recommend allocating **Standard** public IP addresses for all six VMs used in the deployment. At the time of initial publication of this guide, the hourly cost for six such VMs was only $0.008 more than for six VMs with Basic addresses; for current pricing, see the [Microsoft documentation](https://azure.microsoft.com/en-us/pricing/details/ip-addresses/).
- To allocate a **Standard** public IP address, open the **Networking** tab on the **Create a virtual machine** window. Click Create new below the **Public IP** field. In the **Create public IP address** column that opens at right, click the **Standard** radio button under **SKU**. You can change the value in the **Name** field; here we are accepting the default created by Azure, **ngx‑plus‑1‑ip**. Click the ** OK ** button.
+ To allocate a **Standard** public IP address, open the **Networking** tab on the **Create a virtual machine** window. Click Create new below the **Public IP** field. In the {{
@@ -75,7 +75,7 @@ In addition, to install NGINX software by following the linked instructions, you
For simplicity, we recommend allocating **Standard** public IP addresses for all six VMs used in the deployment. At the time of initial publication of this guide, the hourly cost for six such VMs was only $0.008 more than for six VMs with Basic addresses; for current pricing, see the [Microsoft documentation](https://azure.microsoft.com/en-us/pricing/details/ip-addresses/).
- To allocate a **Standard** public IP address, open the **Networking** tab on the **Create a virtual machine** window. Click Create new below the **Public IP** field. In the **Create public IP address** column that opens at right, click the **Standard** radio button under **SKU**. You can change the value in the **Name** field; here we are accepting the default created by Azure, **ngx‑plus‑1‑ip**. Click the ** OK ** button.
+ To allocate a **Standard** public IP address, open the **Networking** tab on the **Create a virtual machine** window. Click Create new below the **Public IP** field. In the {{ @@ -87,7 +87,7 @@ In addition, to install NGINX software by following the linked instructions, you
To change any settings, open the appropriate tab. If the settings are correct, click the Create button.
- If you chose in [Step 4](#create-vm_Basics) to generate a new key pair, a **Generate new key pair** window pops up. Click the Download key and create private resource button.
+ If you chose in [Step 4](#create-vm_Basics) to generate a new key pair, a {{
@@ -87,7 +87,7 @@ In addition, to install NGINX software by following the linked instructions, you
To change any settings, open the appropriate tab. If the settings are correct, click the Create button.
- If you chose in [Step 4](#create-vm_Basics) to generate a new key pair, a **Generate new key pair** window pops up. Click the Download key and create private resource button.
+ If you chose in [Step 4](#create-vm_Basics) to generate a new key pair, a {{ @@ -107,7 +107,7 @@ In addition, to install NGINX software by following the linked instructions, you
For **ngx-plus-2**, it is probably simplest to repeat Steps 2 through 6 above (or purchase a second prebuilt VM in the [Microsoft Azure Marketplace](https://azuremarketplace.microsoft.com/en-us/marketplace/apps?search=NGINX%20Plus)).
- For the NGINX Open Source VMs, you can create them individually using Steps 2 through 6. Alternatively, create them based on an Azure image. To do so, follow Steps 2 through 6 above to create a source VM (naming it **nginx‑oss**), [install the NGINX Open Source software](#install-nginx) on it, and then follow the instructions in [Optional: Creating an NGINX Open Source Image](#create-nginx-oss-image).
+ For the NGINX Open Source VMs, you can create them individually using Steps 2 through 6. Alternatively, create them based on an Azure image. To do so, follow Steps 2 through 6 above to create a source VM (naming it {{
@@ -107,7 +107,7 @@ In addition, to install NGINX software by following the linked instructions, you
For **ngx-plus-2**, it is probably simplest to repeat Steps 2 through 6 above (or purchase a second prebuilt VM in the [Microsoft Azure Marketplace](https://azuremarketplace.microsoft.com/en-us/marketplace/apps?search=NGINX%20Plus)).
- For the NGINX Open Source VMs, you can create them individually using Steps 2 through 6. Alternatively, create them based on an Azure image. To do so, follow Steps 2 through 6 above to create a source VM (naming it **nginx‑oss**), [install the NGINX Open Source software](#install-nginx) on it, and then follow the instructions in [Optional: Creating an NGINX Open Source Image](#create-nginx-oss-image).
+ For the NGINX Open Source VMs, you can create them individually using Steps 2 through 6. Alternatively, create them based on an Azure image. To do so, follow Steps 2 through 6 above to create a source VM (naming it {{ -2. On the page that opens (**ngx‑plus‑1** in this guide), note the VM's public IP address (in the **Public IP address** field in the right column).
+2. On the page that opens ({{
-2. On the page that opens (**ngx‑plus‑1** in this guide), note the VM's public IP address (in the **Public IP address** field in the right column).
+2. On the page that opens ({{ @@ -130,7 +130,7 @@ To install and configure NGINX Open Source or NGINX Plus on a VM, you need to o
where
- - `
@@ -130,7 +130,7 @@ To install and configure NGINX Open Source or NGINX Plus on a VM, you need to o
where
- - ` diff --git a/content/nginx/deployment-guides/single-sign-on/oidc-njs/active-directory-federation-services.md b/content/nginx/deployment-guides/single-sign-on/oidc-njs/active-directory-federation-services.md
index 870198ac6..6d0173780 100644
--- a/content/nginx/deployment-guides/single-sign-on/oidc-njs/active-directory-federation-services.md
+++ b/content/nginx/deployment-guides/single-sign-on/oidc-njs/active-directory-federation-services.md
@@ -50,9 +50,9 @@ The instructions assume you have the following:
Create an AD FS application for NGINX Plus:
-1. Open the AD FS Management window. In the navigation column on the left, right‑click on the **Application Groups** folder and select **Add Application Group** from the drop‑down menu.
+1. Open the AD FS Management window. In the navigation column on the left, right‑click on the **Application Groups** folder and select {{
diff --git a/content/nginx/deployment-guides/single-sign-on/oidc-njs/active-directory-federation-services.md b/content/nginx/deployment-guides/single-sign-on/oidc-njs/active-directory-federation-services.md
index 870198ac6..6d0173780 100644
--- a/content/nginx/deployment-guides/single-sign-on/oidc-njs/active-directory-federation-services.md
+++ b/content/nginx/deployment-guides/single-sign-on/oidc-njs/active-directory-federation-services.md
@@ -50,9 +50,9 @@ The instructions assume you have the following:
Create an AD FS application for NGINX Plus:
-1. Open the AD FS Management window. In the navigation column on the left, right‑click on the **Application Groups** folder and select **Add Application Group** from the drop‑down menu.
+1. Open the AD FS Management window. In the navigation column on the left, right‑click on the **Application Groups** folder and select {{- 2. In the **Redirect URI** field, type the URI of the NGINX Plus instance including the port number, and ending in **/\_codexch**. Here we’re using **https://my‑nginx.example.com:443/\_codexch**. Click the Add button. + 2. In the **Redirect URI** field, type the URI of the NGINX Plus instance including the port number, and ending in **/\_codexch**. Here we’re using {{
 -4. In the **Configure Application Credentials** step, click the **Generate a shared secret** checkbox. Make a note of the secret that AD FS generates (perhaps by clicking the **Copy to clipboard** button and pasting the clipboard content into a file). You will add the secret to the NGINX Plus configuration in [Step 4 of _Configuring NGINX Plus_](#nginx-plus-variables). Click the Next > button.
+4. In the {{
-4. In the **Configure Application Credentials** step, click the **Generate a shared secret** checkbox. Make a note of the secret that AD FS generates (perhaps by clicking the **Copy to clipboard** button and pasting the clipboard content into a file). You will add the secret to the NGINX Plus configuration in [Step 4 of _Configuring NGINX Plus_](#nginx-plus-variables). Click the Next > button.
+4. In the {{ @@ -87,7 +87,7 @@ Create an AD FS application for NGINX Plus:
Configure NGINX Plus as the OpenID Connect relying party:
-1. Create a clone of the [**nginx‑openid‑connect**](https://github.com/nginxinc/nginx-openid-connect) GitHub repository.
+1. Create a clone of the {{
@@ -87,7 +87,7 @@ Create an AD FS application for NGINX Plus:
Configure NGINX Plus as the OpenID Connect relying party:
-1. Create a clone of the [**nginx‑openid‑connect**](https://github.com/nginxinc/nginx-openid-connect) GitHub repository.
+1. Create a clone of the {{ -3. In the **Create a user pool** window that opens, type a value in the **Pool name** field (in this guide, it's **nginx‑plus‑pool**), then click the Review defaults button.
+3. In the **Create a user pool** window that opens, type a value in the **Pool name** field (in this guide, it's {{
-3. In the **Create a user pool** window that opens, type a value in the **Pool name** field (in this guide, it's **nginx‑plus‑pool**), then click the Review defaults button.
+3. In the **Create a user pool** window that opens, type a value in the **Pool name** field (in this guide, it's {{ @@ -70,11 +70,11 @@ Create a new application for NGINX Plus in the Cognito GUI:
5. On the **App clients** tab which opens, click Add an app client.
-6. On the **Which app clients will have access to this user pool?** window which opens, enter a value (in this guide, **nginx‑plus‑app**) in the **App client name** field. Make sure the **Generate client secret** box is checked, then click the Create app client button.
+6. On the **Which app clients will have access to this user pool?** window which opens, enter a value (in this guide, {{
@@ -70,11 +70,11 @@ Create a new application for NGINX Plus in the Cognito GUI:
5. On the **App clients** tab which opens, click Add an app client.
-6. On the **Which app clients will have access to this user pool?** window which opens, enter a value (in this guide, **nginx‑plus‑app**) in the **App client name** field. Make sure the **Generate client secret** box is checked, then click the Create app client button.
+6. On the **Which app clients will have access to this user pool?** window which opens, enter a value (in this guide, {{ -7. On the confirmation page which opens, click **Return to pool details** to return to the **Review** tab. On that tab click the Create pool button at the bottom. (The screenshot in [Step 4](#cognito-review-tab) shows the button.)
+7. On the confirmation page which opens, click {{
-7. On the confirmation page which opens, click **Return to pool details** to return to the **Review** tab. On that tab click the Create pool button at the bottom. (The screenshot in [Step 4](#cognito-review-tab) shows the button.)
+7. On the confirmation page which opens, click {{ -9. Click **Users and groups** in the left navigation column. In the interface that opens, designate the users (or group of users, on the **Groups** tab) who will be able to use SSO for the app being proxied by NGINX Plus. For instructions, see the Cognito documentation about [creating users](https://docs.aws.amazon.com/cognito/latest/developerguide/how-to-create-user-accounts.html), [importing users](https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-using-import-tool.html), or [adding a group](https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-user-groups.html).
+9. Click {{
-9. Click **Users and groups** in the left navigation column. In the interface that opens, designate the users (or group of users, on the **Groups** tab) who will be able to use SSO for the app being proxied by NGINX Plus. For instructions, see the Cognito documentation about [creating users](https://docs.aws.amazon.com/cognito/latest/developerguide/how-to-create-user-accounts.html), [importing users](https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-using-import-tool.html), or [adding a group](https://docs.aws.amazon.com/cognito/latest/developerguide/cognito-user-pools-user-groups.html).
+9. Click {{ -10. Click **App clients** in the left navigation bar. On the tab that opens, click the Show Details button in the box labeled with the app client name (in this guide, **nginx‑plus‑app**).
+10. Click **App clients** in the left navigation bar. On the tab that opens, click the Show Details button in the box labeled with the app client name (in this guide, {{
-10. Click **App clients** in the left navigation bar. On the tab that opens, click the Show Details button in the box labeled with the app client name (in this guide, **nginx‑plus‑app**).
+10. Click **App clients** in the left navigation bar. On the tab that opens, click the Show Details button in the box labeled with the app client name (in this guide, {{ -11. On the details page that opens, make note of the values in the **App client id** and **App client secret** fields. You will add them to the NGINX Plus configuration in [Step 3 of _Configuring NGINX Plus_](#nginx-plus-variables).
+11. On the details page that opens, make note of the values in the {{
-11. On the details page that opens, make note of the values in the **App client id** and **App client secret** fields. You will add them to the NGINX Plus configuration in [Step 3 of _Configuring NGINX Plus_](#nginx-plus-variables).
+11. On the details page that opens, make note of the values in the {{ -12. Click **App client settings** in the left navigation column. In the tab that opens, perform the following steps:
+12. Click {{
-12. Click **App client settings** in the left navigation column. In the tab that opens, perform the following steps:
+12. Click {{ -13. Click **Domain name** in the left navigation column. In the tab that opens, type a domain prefix in the **Domain prefix** field under **Amazon Cognito domain** (in this guide, **my‑nginx‑plus**). Click the Save changes button.
+13. Click **Domain name** in the left navigation column. In the tab that opens, type a domain prefix in the **Domain prefix** field under {{
-13. Click **Domain name** in the left navigation column. In the tab that opens, type a domain prefix in the **Domain prefix** field under **Amazon Cognito domain** (in this guide, **my‑nginx‑plus**). Click the Save changes button.
+13. Click **Domain name** in the left navigation column. In the tab that opens, type a domain prefix in the **Domain prefix** field under {{ @@ -120,7 +120,7 @@ Create a new application for NGINX Plus in the Cognito GUI:
Configure NGINX Plus as the OpenID Connect relying party:
-1. Create a clone of the [**nginx‑openid‑connect**](https://github.com/nginxinc/nginx-openid-connect) GitHub repository.
+1. Create a clone of the {{
@@ -120,7 +120,7 @@ Create a new application for NGINX Plus in the Cognito GUI:
Configure NGINX Plus as the OpenID Connect relying party:
-1. Create a clone of the [**nginx‑openid‑connect**](https://github.com/nginxinc/nginx-openid-connect) GitHub repository.
+1. Create a clone of the {{ 4. On the **NGINX Plus** page that opens, enter or select these values on the Settings tab:
- **Access Type** – **confidential**
- - **Valid Redirect URIs** – The URI of the NGINX Plus instance, including the port number, and ending in **/\_codexch** (in this guide it is **https://my‑nginx.example.com:443/_codexch**)
+ - **Valid Redirect URIs** – The URI of the NGINX Plus instance, including the port number, and ending in **/\_codexch** (in this guide it is {{
4. On the **NGINX Plus** page that opens, enter or select these values on the Settings tab:
- **Access Type** – **confidential**
- - **Valid Redirect URIs** – The URI of the NGINX Plus instance, including the port number, and ending in **/\_codexch** (in this guide it is **https://my‑nginx.example.com:443/_codexch**)
+ - **Valid Redirect URIs** – The URI of the NGINX Plus instance, including the port number, and ending in **/\_codexch** (in this guide it is {{ 8. In the left navigation column, click **Users**. On the **Users** page that opens, either click the name of an existing user, or click the **Add user** button in the upper right corner to create a new user. For complete instructions, see the [Keycloak documentation](https://www.keycloak.org/docs/latest/server_admin/index.html#user-management).
-9. On the management page for the user (here, **user01**), click the Role Mappings tab. On the page that opens, select **NGINX‑Plus** on the **Client Roles** drop‑down menu. Click **nginx‑keycloak‑role** in the **Available Roles** box, then click the **Add selected** button below the box. The role then appears in the **Assigned Roles** and **Effective Roles** boxes, as shown in the screenshot.
+9. On the management page for the user (here, **user01**), click the Role Mappings tab. On the page that opens, select {{
8. In the left navigation column, click **Users**. On the **Users** page that opens, either click the name of an existing user, or click the **Add user** button in the upper right corner to create a new user. For complete instructions, see the [Keycloak documentation](https://www.keycloak.org/docs/latest/server_admin/index.html#user-management).
-9. On the management page for the user (here, **user01**), click the Role Mappings tab. On the page that opens, select **NGINX‑Plus** on the **Client Roles** drop‑down menu. Click **nginx‑keycloak‑role** in the **Available Roles** box, then click the **Add selected** button below the box. The role then appears in the **Assigned Roles** and **Effective Roles** boxes, as shown in the screenshot.
+9. On the management page for the user (here, **user01**), click the Role Mappings tab. On the page that opens, select {{ @@ -101,7 +101,7 @@ Create a Keycloak client for NGINX Plus in the Keycloak GUI:
Configure NGINX Plus as the OpenID Connect relying party:
-1. Create a clone of the [**nginx‑openid‑connect**](https://github.com/nginxinc/nginx-openid-connect) GitHub repository.
+1. Create a clone of the {{
@@ -101,7 +101,7 @@ Create a Keycloak client for NGINX Plus in the Keycloak GUI:
Configure NGINX Plus as the OpenID Connect relying party:
-1. Create a clone of the [**nginx‑openid‑connect**](https://github.com/nginxinc/nginx-openid-connect) GitHub repository.
+1. Create a clone of the {{ -3. On the **Find Applications** page that opens, type **OpenID Connect** in the search box. Click on the **OpenID Connect (OIDC)** row that appears.
+3. On the **Find Applications** page that opens, type {{
-3. On the **Find Applications** page that opens, type **OpenID Connect** in the search box. Click on the **OpenID Connect (OIDC)** row that appears.
+3. On the **Find Applications** page that opens, type {{ -4. On the **Add OpenId Connect (OIDC)** page that opens, change the value in the **Display Name** field to **NGINX Plus** and click the Save button.
+4. On the **Add OpenId Connect (OIDC)** page that opens, change the value in the **Display Name** field to {{
-4. On the **Add OpenId Connect (OIDC)** page that opens, change the value in the **Display Name** field to **NGINX Plus** and click the Save button.
+4. On the **Add OpenId Connect (OIDC)** page that opens, change the value in the **Display Name** field to {{ -5. When the save completes, a new set of choices appears in the left navigation bar. Click **Configuration**. In the **Redirect URI's** field, type the URI of the NGINX Plus instance including the port number, and ending in **/\_codexch** (in this guide it is **https://my‑nginx.example.com:443/_codexch**). Then click the Save button.
+5. When the save completes, a new set of choices appears in the left navigation bar. Click **Configuration**. In the **Redirect URI's** field, type the URI of the NGINX Plus instance including the port number, and ending in **/\_codexch** (in this guide it is {{
-5. When the save completes, a new set of choices appears in the left navigation bar. Click **Configuration**. In the **Redirect URI's** field, type the URI of the NGINX Plus instance including the port number, and ending in **/\_codexch** (in this guide it is **https://my‑nginx.example.com:443/_codexch**). Then click the Save button.
+5. When the save completes, a new set of choices appears in the left navigation bar. Click **Configuration**. In the **Redirect URI's** field, type the URI of the NGINX Plus instance including the port number, and ending in **/\_codexch** (in this guide it is {{ -6. When the save completes, click **SSO** in the left navigation bar. Click **Show client secret** below the **Client Secret** field. Record the values in the **Client ID** and **Client Secret** fields. You will add them to the NGINX Plus configuration in [Step 4 of _Configuring NGINX Plus_](#nginx-plus-variables).
+6. When the save completes, click **SSO** in the left navigation bar. Click {{
-6. When the save completes, click **SSO** in the left navigation bar. Click **Show client secret** below the **Client Secret** field. Record the values in the **Client ID** and **Client Secret** fields. You will add them to the NGINX Plus configuration in [Step 4 of _Configuring NGINX Plus_](#nginx-plus-variables).
+6. When the save completes, click **SSO** in the left navigation bar. Click {{ -7. Assign users to the application (in this guide, **NGINX Plus**) to enable them to access it for SSO. OneLogin recommends using [roles](https://onelogin.service-now.com/kb_view_customer.do?sysparm_article=KB0010606) for this purpose. You can access the **Roles** page under Users in the title bar.
+7. Assign users to the application (in this guide, {{
-7. Assign users to the application (in this guide, **NGINX Plus**) to enable them to access it for SSO. OneLogin recommends using [roles](https://onelogin.service-now.com/kb_view_customer.do?sysparm_article=KB0010606) for this purpose. You can access the **Roles** page under Users in the title bar.
+7. Assign users to the application (in this guide, {{ diff --git a/content/nginx/deployment-guides/single-sign-on/oidc-njs/ping-identity.md b/content/nginx/deployment-guides/single-sign-on/oidc-njs/ping-identity.md
index d4901c65a..495b2ebad 100644
--- a/content/nginx/deployment-guides/single-sign-on/oidc-njs/ping-identity.md
+++ b/content/nginx/deployment-guides/single-sign-on/oidc-njs/ping-identity.md
@@ -56,30 +56,30 @@ Create a new application for NGINX Plus:
1. Log in to your Ping Identity account. The administrative dashboard opens automatically. In this guide, we show the PingOne for Enterprise dashboard, and for brevity refer simply to ”PingOne”.
-2. Click APPLICATIONS in the title bar, and on the **My Applications** page that opens, click **OIDC** and then the **+ Add Application** button.
+2. Click APPLICATIONS in the title bar, and on the **My Applications** page that opens, click **OIDC** and then the {{
diff --git a/content/nginx/deployment-guides/single-sign-on/oidc-njs/ping-identity.md b/content/nginx/deployment-guides/single-sign-on/oidc-njs/ping-identity.md
index d4901c65a..495b2ebad 100644
--- a/content/nginx/deployment-guides/single-sign-on/oidc-njs/ping-identity.md
+++ b/content/nginx/deployment-guides/single-sign-on/oidc-njs/ping-identity.md
@@ -56,30 +56,30 @@ Create a new application for NGINX Plus:
1. Log in to your Ping Identity account. The administrative dashboard opens automatically. In this guide, we show the PingOne for Enterprise dashboard, and for brevity refer simply to ”PingOne”.
-2. Click APPLICATIONS in the title bar, and on the **My Applications** page that opens, click **OIDC** and then the **+ Add Application** button.
+2. Click APPLICATIONS in the title bar, and on the **My Applications** page that opens, click **OIDC** and then the {{ -3. The **Add OIDC Application** window pops up. Click the ADVANCED CONFIGURATION box, and then the Next button.
+3. The {{
-3. The **Add OIDC Application** window pops up. Click the ADVANCED CONFIGURATION box, and then the Next button.
+3. The {{ -4. In section 1 (PROVIDE DETAILS ABOUT YOUR APPLICATION), type a name in the **APPLICATION NAME** field and a short description in the **SHORT DESCRIPTION** field. Here, we're using **nginx‑plus‑application** and **NGINX Plus**. Choose a value from the **CATEGORY** drop‑down menu; here we’re using **Information Technology**. You can also add an icon if you wish. Click the Next button.
+4. In section 1 (PROVIDE DETAILS ABOUT YOUR APPLICATION), type a name in the **APPLICATION NAME** field and a short description in the **SHORT DESCRIPTION** field. Here, we're using {{
-4. In section 1 (PROVIDE DETAILS ABOUT YOUR APPLICATION), type a name in the **APPLICATION NAME** field and a short description in the **SHORT DESCRIPTION** field. Here, we're using **nginx‑plus‑application** and **NGINX Plus**. Choose a value from the **CATEGORY** drop‑down menu; here we’re using **Information Technology**. You can also add an icon if you wish. Click the Next button.
+4. In section 1 (PROVIDE DETAILS ABOUT YOUR APPLICATION), type a name in the **APPLICATION NAME** field and a short description in the **SHORT DESCRIPTION** field. Here, we're using {{ 5. In section 2 (AUTHORIZATION SETTINGS), perform these steps:
- 1. Under **GRANTS**, click both **Authorization Code** and **Implicit**.
5. In section 2 (AUTHORIZATION SETTINGS), perform these steps:
- 1. Under **GRANTS**, click both **Authorization Code** and **Implicit**.- 2. Under **CREDENTIALS**, click the **+ Add Secret** button. PingOne creates a client secret and opens the **CLIENT SECRETS** field to display it, as shown in the screenshot. To see the actual value of the secret, click the eye icon.
+ 1. Under **GRANTS**, click both {{
+ 2. Under **CREDENTIALS**, click the {{
3. Click the Next button.
 6. In section 3 (SSO FLOW AND AUTHENTICATION SETTINGS):
- 1. In the **START SSO URL** field, type the URL where users access your application. Here we’re using **https://example.com**.
- 2. In the **REDIRECT URIS** field, type the URI of the NGINX Plus instance including the port number, and ending in **/\_codexch**. Here we’re using **https://my‑nginx‑plus.example.com:443/\_codexch** (the full value is not visible in the screenshot).
+ 1. In the {{
6. In section 3 (SSO FLOW AND AUTHENTICATION SETTINGS):
- 1. In the **START SSO URL** field, type the URL where users access your application. Here we’re using **https://example.com**.
- 2. In the **REDIRECT URIS** field, type the URI of the NGINX Plus instance including the port number, and ending in **/\_codexch**. Here we’re using **https://my‑nginx‑plus.example.com:443/\_codexch** (the full value is not visible in the screenshot).
+ 1. In the {{ -7. In section 4 (DEFAULT USER PROFILE ATTRIBUTE CONTRACT), optionally add attributes to the required **sub** and **idpid** attributes, by clicking the **+ Add Attribute** button. We’re not adding any in this example. When finished, click the Next button.
+7. In section 4 (DEFAULT USER PROFILE ATTRIBUTE CONTRACT), optionally add attributes to the required **sub** and **idpid** attributes, by clicking the {{
-7. In section 4 (DEFAULT USER PROFILE ATTRIBUTE CONTRACT), optionally add attributes to the required **sub** and **idpid** attributes, by clicking the **+ Add Attribute** button. We’re not adding any in this example. When finished, click the Next button.
+7. In section 4 (DEFAULT USER PROFILE ATTRIBUTE CONTRACT), optionally add attributes to the required **sub** and **idpid** attributes, by clicking the {{ -8. In section 5 (CONNECT SCOPES), click the circled plus-sign on the **OpenID Profile (profile)** and **OpenID Profile Email (email)** scopes in the **LIST OF SCOPES** column. They are moved to the **CONNECTED SCOPES** column, as shown in the screenshot. Click the Next button.
+8. In section 5 (CONNECT SCOPES), click the circled plus-sign on the {{
-8. In section 5 (CONNECT SCOPES), click the circled plus-sign on the **OpenID Profile (profile)** and **OpenID Profile Email (email)** scopes in the **LIST OF SCOPES** column. They are moved to the **CONNECTED SCOPES** column, as shown in the screenshot. Click the Next button.
+8. In section 5 (CONNECT SCOPES), click the circled plus-sign on the {{ @@ -107,14 +107,14 @@ Create a new application for NGINX Plus:
@@ -107,14 +107,14 @@ Create a new application for NGINX Plus:
 -11. You are returned to the **My Applications** window, which now includes a row for **nginx‑plus‑application**. Click the toggle switch at the right end of the row to the “on” position, as shown in the screenshot. Then click the “expand” icon at the end of the row, to display the application’s details.
+11. You are returned to the **My Applications** window, which now includes a row for {{
-11. You are returned to the **My Applications** window, which now includes a row for **nginx‑plus‑application**. Click the toggle switch at the right end of the row to the “on” position, as shown in the screenshot. Then click the “expand” icon at the end of the row, to display the application’s details.
+11. You are returned to the **My Applications** window, which now includes a row for {{ 12. On the page that opens, make note of the values in the following fields on the **Details** tab. You will add them to the NGINX Plus configuration in [Step 4 of _Configuring NGINX Plus_](#nginx-plus-variables).
- - **CLIENT ID** (in the screenshot, **28823604‑83c5‑4608‑88da‑c73fff9c607a**)
+ - **CLIENT ID** (in the screenshot, {{
12. On the page that opens, make note of the values in the following fields on the **Details** tab. You will add them to the NGINX Plus configuration in [Step 4 of _Configuring NGINX Plus_](#nginx-plus-variables).
- - **CLIENT ID** (in the screenshot, **28823604‑83c5‑4608‑88da‑c73fff9c607a**)
+ - **CLIENT ID** (in the screenshot, {{ @@ -124,7 +124,7 @@ Create a new application for NGINX Plus:
Configure NGINX Plus as the OpenID Connect relying party:
-1. Create a clone of the [**nginx‑openid‑connect**](https://github.com/nginxinc/nginx-openid-connect) GitHub repository.
+1. Create a clone of the {{
@@ -124,7 +124,7 @@ Create a new application for NGINX Plus:
Configure NGINX Plus as the OpenID Connect relying party:
-1. Create a clone of the [**nginx‑openid‑connect**](https://github.com/nginxinc/nginx-openid-connect) GitHub repository.
+1. Create a clone of the {{- **Offline**: NGINX Agent is connected but the NGINX instance isn't running, isn't installed, or can't communicate with NGINX Agent.
- **Unavailable**: The connection between NGINX Agent and NGINX One has been lost or the instance has been decommissioned.
- **Unknown**: The current state can't be determined at the moment. | +| **NGINX versions by instance** | See which NGINX versions are in use across your instances. | | +| **Operating systems** | Find out which operating systems your instances are running on. | | +| **Certificates** | Monitor the status of your SSL certificates to know which are expiring soon and which are still valid. | | +| **Config recommendations** | Get configuration recommendations to optimize your instances' settings. | | +| **CVEs (Common Vulnerabilities and Exposures)** | Evaluate the severity and number of potential security threats in your instances. | - **Major**: Indicates a high-severity threat that needs immediate attention.
- **Medium**: Implies a moderate threat level.
- **Minor** and **Low**: Represent less critical issues that still require monitoring.
- **Other**: Encompasses any threats that don't fit the standard categories. | +| **CPU utilization** | Track CPU usage trends and pinpoint instances with high CPU demand. | | +| **Memory utilization** | Watch memory usage patterns to identify instances using significant memory. | | +| **Disk space utilization** | Monitor how much disk space your instances are using and identify those nearing capacity. | | +| **Unsuccessful response codes** | Look for instances with a high number of HTTP server errors and investigate their error codes. | | +| **Top network usage** | Review the network usage and bandwidth consumption of your instances. | | + +{{
+ {{ .Title }} +
+ {{ if .Description }} ++ {{ .Description | markdownify }} +
+ {{ end}} + {{ if .Content }} ++ {{ .Content | markdownify }} +
+ {{ end }} ++ + {{ .Title }} +
+ {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Manage your NGINX fleet")}} +Simplify, scale, secure, and collaborate with your NGINX fleet
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Get started")}} +See benefits from the NGINX One Console
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Draft new configurations")}} +Work with Staged Configurations
+ {{ end }} + + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Manage your NGINX instances")}} +Monitor and maintain your deployments
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Organize users with RBAC")}} +Assign responsibilities with role-based access control
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Automate with the NGINX One API")}} +Manage your NGINX fleet over REST
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Glossary")}} +Learn terms unique to NGINX One Console
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Connect your instances") }} +Work with data plane keys, containers, and proxy servers
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Set up metrics") }} +Review your deployments in a dashboard
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "API")}} +These are API docs
+-
+ {{ range .Pages }}
+
- {{ .Title }} + {{ end }} +
Other Products
+ {{ $nginxProducts := slice + (dict "title" "NGINX Instance Manager" "url" "/nginx-instance-manager" "imgSrc" "NGINX-Instance-Manager-product-icon" "type" "local-console-option" "description" "Track and control NGINX Open Source and NGINX Plus instances.") + (dict "title" "NGINX Ingress Controller" "url" "/nginx-ingress-controller" "imgSrc" "NGINX-Ingress-Controller-product-icon" "type" "kubernetes-solutions" "description" "Kubernetes traffic management with API gateway, identity, and observability features.") + (dict "title" "NGINX Gateway Fabric" "url" "/nginx-gateway-fabric" "imgSrc" "NGINX-product-icon" "type" "kubernetes-solutions" "description" "Next generation Kubernetes connectivity using the Gateway API.") + (dict "title" "NGINX App Protect WAF" "url" "/nginx-app-protect-waf" "imgSrc" "NGINX-App-Protect-WAF-product-icon" "type" "security" "description" "Lightweight, high-performance, advanced protection against Layer 7 attacks on your apps and APIs.") + (dict "title" "NGINX App Protect DoS" "url" "/nginx-app-protect-dos" "imgSrc" "NGINX-App-Protect-DoS-product-icon" "type" "security" "description" "Defend, adapt, and mitigate against Layer 7 denial-of-service attacks on your apps and APIs.") + (dict "title" "NGINX Plus" "url" "/nginx" "imgSrc" "NGINX-Plus-product-icon-RGB" "type" "modern-app-delivery" "description" "The all-in-one load balancer, reverse proxy, web server, content cache, and API gateway.") + (dict "title" "NGINX Open Source" "url" "https://nginx.org/en/docs/" "imgSrc" "NGINX-product-icon" "type" "modern-app-delivery" "description" "The open source all-in-one load balancer, content cache, and web server") + }} + {{ $groupedProducts := dict + "local-console-option" (where $nginxProducts "type" "local-console-option") + "kubernetes-solutions" (where $nginxProducts "type" "kubernetes-solutions") + "security" (where $nginxProducts "type" "security") + "modern-app-delivery" (where $nginxProducts "type" "modern-app-delivery") + }} + {{ range $type, $products := $groupedProducts }} +{{ $type | humanize | title }}
+ {{ range $products }} +
+  + {{ .title }}
+
+ {{ .title }}
+
+ + {{ if .description }}{{ .description | markdownify }}{{ end }} +
+- For more details about usage reporting and enforcement, see [About solution licenses](../../../../solutions/about-subscription-licenses) + For more details about usage reporting and enforcement, see [About solution licenses]({{< ref "/solutions/about-subscription-licenses.md" >}}) {{}} \ No newline at end of file From c2a7f674dfedba9e72250cc289c34c47bfbcedce Mon Sep 17 00:00:00 2001 From: yar
/etc/nginx/ssl/example.com.key | Typically purchased from a Certificate Authority (CA) | +| Repository access | /etc/ssl/nginx/nginx-repo.crt
/etc/ssl/nginx/nginx-repo.key | Supports access to repositories to download and install NGINX packages | +| NGINX Licensing | /etc/ssl/nginx/server.crt
/etc/ssl/nginx/server.key | Supports access to repositories. Based on licenses downloaded from https://my.f5.com/ | +{{
+ +To create a security policy using the Instance Manager web interface: + +1. In a web browser, go to the FQDN for your NGINX Management Suite host and log in. Then, from the Launchpad menu, select **Instance Manager**. +2. On the left menu, select **App Protect**. +3. On the *Security Policies* page, select **Create**. +4. On the *Create Policy* page, fill out the necessary fields: -1. In your browser, go to the FQDN for your NGINX Instance Manager host and log in. -2. From the Launchpad menu, select **Instance Manager**. -3. In the left menu, select **App Protect**. -4. On the *Security Policies* page, select **Create**. -5. On the *Create Policy* page, enter the required information: - - **Name**: Enter a name for the policy. - - **Description**: (Optional) Add a brief description. - - **Enter Policy**: Paste or type the JSON-formatted policy into the editor. The interface automatically validates the JSON. + - **Name**: Provide a name for the policy. + - **Description**: (Optional) Add a short description for the policy. + - **Enter Policy**: Type or paste the policy in JSON format into the form provided. The editor will validate the JSON for accuracy. - For help writing custom policies, see the [NGINX App Protect WAF Declarative Policy guide](https://docs.nginx.com/nginx-app-protect/declarative-policy/policy/) and the [Policy Authoring and Tuning section](https://docs.nginx.com/nginx-app-protect/configuration-guide/configuration/#policy-authoring-and-tuning) in the configuration guide. + For more information about creating custom policies, refer to the [NGINX App Protect WAF Declarative Policy](https://docs.nginx.com/nginx-app-protect/declarative-policy/policy/) guide and the [Policy Authoring and Tuning](https://docs.nginx.com/nginx-app-protect/configuration-guide/configuration/#policy-authoring-and-tuning) section of the config guide. -6. Select **Save**. +5. Select **Save**. {{%/tab%}} {{%tab name="API"%}} -To upload a new security policy using the REST API, send a `POST` request to the Security Policies API endpoint. +To upload a new security policy, send an HTTP `POST` request to the Security Policies API endpoint. + +{{
-You must encode the JSON policy using `base64`. If you send the policy in plain JSON, the request will fail. {{
-To delete a security policy using the NGINX Instance Manager web interface: - -1. In your browser, go to the FQDN for your NGINX Instance Manager host and log in. -2. From the Launchpad menu, select **Instance Manager**. -3. In the left menu, select **App Protect**. -4. On the *Security Policies* page, find the policy you want to delete. -5. Select the **Actions** menu (**...**) and choose **Delete**. +To delete a security policy using the Instance Manager web interface: +1. In a web browser, go to the FQDN for your NGINX Management Suite host and log in. Then, from the Launchpad menu, select **Instance Manager**. +2. On the left menu, select **App Protect**. +3. On the *Security Policies* page, select the **Actions** menu (represented by an ellipsis, **...**) for the policy you want to delete. Select **Delete** to remove the policy. {{%/tab%}} {{%tab name="API"%}} -To delete a security policy using the REST API: - -1. Retrieve the UID for the policy by sending a `GET` request to the policies endpoint: - - ```shell - curl -X GET https://{{NIM_FQDN}}/api/platform/v1/security/policies \ - -H "Authorization: Bearer
{{
{{
-You must encode the log profile in `base64` before sending it. If you send plain JSON, the request will fail. {{
JSON Response
+```json +{ + "associations": [ + { + "attackSignatureLibrary": { + "uid": "c69460cc-6b59-4813-8d9c-76e4a6c56b4b", + "versionDateTime": "2023.02.16" + }, + "instance": { + "hostName": "ip-172-16-0-99", + "lastDeploymentDetails": { + "createTime": "2023-04-11T21:36:11.519174534Z", + "details": { + "failure": [], + "pending": [], + "success": [ + { + "name": "ip-172-16-0-99" + } + ] + }, + "id": "19cf5ed4-29d6-4139-b5f5-308c0d0ebb13", + "message": "Instance config successfully published to", + "status": "successful", + "updateTime": "2023-04-11T21:36:14.008108979Z" + }, + "systemUid": "0435a5de-41c1-3754-b2e8-9d9fe946bafe", + "uid": "29d86fe8-612a-5c69-895a-04fc5b9849a6" + }, + "instanceGroup": { + "displayName": "inst_group_1", + "instances": [ + { + "hostName": "hostname1", + "systemUid": "49d143c2-f556-4cd7-8658-76fff54fb861", + "uid": "c8e15dcf-c504-4b7f-b52d-def7b8fd2f64", + "lastDeploymentDetails": { + "createTime": "2023-04-11T21:36:11.519174534Z", + "details": { + "failure": [], + "pending": [], + "success": [ + { + "name": "ip-172-16-0-99" + } + ] + }, + "id": "19cf5ed4-29d6-4139-b5f5-308c0d0ebb13", + "message": "Instance config successfully published to", + "status": "successful", + "updateTime": "2023-04-11T21:36:14.008108979Z" + }, + }, + { + "hostName": "hostname2", + "systemUid": "88a99ab0-15bb-4719-9107-daf5007c33f7", + "uid": "ed7e9173-794f-41af-80d9-4ed37d593247", + "lastDeploymentDetails": { + "createTime": "2023-04-11T21:36:11.519174534Z", + "details": { + "failure": [], + "pending": [], + "success": [ + { + "name": "ip-172-16-0-99" + } + ] + }, + "id": "19cf5ed4-29d6-4139-b5f5-308c0d0ebb13", + "message": "Instance config successfully published to", + "status": "successful", + "updateTime": "2023-04-11T21:36:14.008108979Z" + }, + } + ], + "uid": "51f8addc-c0e9-438b-b0b6-3e4f1aa8202d" + }, + "policyUid": "9991f237-d9c7-47b7-98aa-faa836838f38", + "policyVersionDateTime": "2023-04-11T21:18:19.183Z", + "threatCampaign": { + "uid": "eab683fe-c2f1-4910-a88c-8bfbc6363164", + "versionDateTime": "2023.02.15" + } + } + ] +} +``` -### Check publication status for a security log profile +JSON Response
-### Check status for a specific instance +```json +{ + "associations": [ + { + "instance": { + "hostName": "", + "systemUid": "", + "uid": "" + }, + "instanceGroup": { + "displayName": "ig1", + "instances": [ + { + "hostName": "ip-172-16-0-142", + "systemUid": "1d1f03ff-02de-32c5-8dfd-902658aada4c", + "uid": "18d074e6-3868-51ba-9999-b7466a936815" + } + ], + "lastDeploymentDetails": { + "createTime": "2023-07-05T23:01:06.679136973Z", + "details": { + "failure": [], + "pending": [], + "success": [ + { + "name": "ip-172-16-0-142" + } + ] + }, + "id": "9bfc9db7-877d-4e8e-a43d-9660a6cd11cc", + "message": "Instance Group config successfully published to ig1", + "status": "successful", + "updateTime": "2023-07-05T23:01:06.790802157Z" + }, + "uid": "0df0386e-82f7-4efc-863e-5d7cfbc3f7df" + }, + "logProfileUid": "b680f7c3-6fc0-4c6b-889a-3025580c7fcb", + "logProfileVersionDateTime": "2023-07-05T22:08:47.371Z" + }, + { + "instance": { + "hostName": "ip-172-16-0-5", + "lastDeploymentDetails": { + "createTime": "2023-07-05T21:45:08.698646791Z", + "details": { + "failure": [], + "pending": [], + "success": [ + { + "name": "ip-172-16-0-5" + } + ] + }, + "id": "73cf670a-738a-4a74-b3fb-ac9771e89814", + "message": "Instance config successfully published to", + "status": "successful", + "updateTime": "2023-07-05T21:45:08.698646791Z" + }, + "systemUid": "0afe5ac2-43aa-36c8-bcdc-7f88cdd35ab2", + "uid": "9bb4e2ef-3746-5d79-b526-e545fad27e90" + }, + "instanceGroup": { + "displayName": "", + "instances": [], + "uid": "" + }, + "logProfileUid": "bb3badb2-f8f5-4b95-9428-877fc208e2f1", + "logProfileVersionDateTime": "2023-07-03T21:46:17.006Z" + } + ] +} +``` -You can also view the deployment status for a specific instance by providing the system UID and instance UID. +JSON Response
-### Check deployment result by deployment ID +```json +{ + "build": { + "nginxPlus": true, + "release": "nginx-plus-r28", + "version": "1.23.2" + }, + "configPath": "/etc/nginx/nginx.conf", + "configVersion": { + "instanceGroup": { + "createTime": "0001-01-01T00:00:00Z", + "uid": "", + "versionHash": "" + }, + "versions": [ + { + "createTime": "2023-01-14T10:48:46.319Z", + "uid": "5663cf4e-a0c7-50c8-b93c-16fd11a0f00b", + "versionHash": "922e9d40fa6d4dd3a4b721295b8ecd95f73402644cb8d234f9f4f862b8a56bfc" + } + ] + }, + "displayName": "ip-192-0-2-27", + "links": [ + { + "rel": "/api/platform/v1/systems/b9df6377-2c4f-3266-a64a-e064b0371c73", + "name": "system" + }, + { + "rel": "/api/platform/v1/systems/b9df6377-2c4f-3266-a64a-e064b0371c73/instances/5663cf4e-a0c7-50c8-b93c-16fd11a0f00b", + "name": "self" + }, + { + "rel": "/api/platform/v1/systems/instances/deployments/b31c6ab1-4a46-4c81-a065-204575145e8e", + "name": "deployment" + } + ], + "processPath": "/usr/sbin/nginx", + "registrationTime": "2023-01-14T10:12:31.000Z", + "startTime": "2023-01-14T10:09:43Z", + "status": { + "lastStatusReport": "2023-01-14T11:11:49.323495017Z", + "state": "online" + }, + "uid": "5663cf4e-a0c7-50c8-b93c-16fd11a0f00b", + "version": "1.23.2", + "appProtect": { + "attackSignatureVersion": "Available after publishing Attack Signatures from Instance Manager", + "status": "active", + "threatCampaignVersion": "Available after publishing Threat Campaigns from Instance Manager", + "version": "4.2.0" + }, + "configureArgs": [ + ... + ], + "lastDeploymentDetails": { + "createTime": "2023-01-14T11:10:25.096812852Z", + "details": { + "error": "{\"instance:b9df6377-2c4f-3266-a64a-e064b0371c73\":\"failed building config payload: policy compilation failed for deployment b31c6ab1-4a46-4c81-a065-204575145e8e due to integrations service error: the specified compiler (4.2.0) is missing, please install it and try again.\"}", + "failure": [ + { + "failMessage": "failed building config payload: policy compilation failed for deployment b31c6ab1-4a46-4c81-a065-204575145e8e due to integrations service error: the specified compiler (4.2.0) is missing, please install it and try again.", + "name": "ip-192-0-2-27" + } + ], + "pending": [], + "success": [] + }, + "id": "b31c6ab1-4a46-4c81-a065-204575145e8e", + "message": "Instance config failed to publish to", + "status": "failed", + "updateTime": "2023-01-14T11:10:25.175145693Z" + }, + "loadableModules": [ + ... + ], + "packages": [ + ... + ], + "processId": "10345", + "ssl": { + "built": null, + "runtime": null + } +} +``` -When you use the Publish API to [publish security content](#publish-policy), NGINX Instance Manager creates a deployment ID for the request. You can use this ID to check the result of the publication. +JSON Response
+ +```json +{ + "createTime": "2023-01-14T04:35:47.566082799Z", + "details": { + "error": "{\"instance:8a2092aa-5612-370d-bff0-5d7521e206d6\":\"failed building config payload: policy bundle compilation failed for d38a8e5d-2312-4046-a60f-a30a4aea1fbb, integrations service returned the following error: missing the specified compiler (4.2.0) please install it and try again\"}", + "failure": [ + { + "failMessage": "failed building config payload: policy bundle compilation failed for d38a8e5d-2312-4046-a60f-a30a4aea1fbb, integrations service returned the following error: missing the specified compiler (4.2.0) please install it and try again", + "name": "ip-192-0-2-243" + } + ], + "pending": [], + "success": [] + }, + "id": "d38a8e5d-2312-4046-a60f-a30a4aea1fbb", + "message": "Instance config failed to publish to", + "status": "failed", + "updateTime": "2023-01-14T04:35:47.566082799Z" +} +``` + +{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Draft new configurations")}}
Work with Staged Configurations
{{ end }} +<<<<<<< HEAD {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Manage your NGINX instances")}}Monitor and maintain your deployments
+======= + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Watch your NGINX instances")}} +Keep an inventory of your deployments
+>>>>>>> 09d8a53f (More) {{ end }} {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Organize users with RBAC")}}Assign responsibilities with role-based access control
{{ end }} +<<<<<<< HEAD {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Automate with the NGINX One API")}}Manage your NGINX fleet over REST
+======= + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Organize your administrators with RBAC")}} +Secure your systems with role-based access control
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Change multiple instances with one push")}} +Configure and synchronize groups of NGINX instances simultaneously
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "NGINX One API")}} +Automate NGINX fleet management
+>>>>>>> 09d8a53f (More) {{ end }} {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Glossary")}}Learn terms unique to NGINX One Console
From 39acb8d04c46a6bb453cb4b05c9b722f347b86c5 Mon Sep 17 00:00:00 2001 From: Mike Jang <3287976+mjang@users.noreply.github.com> Date: Fri, 25 Apr 2025 11:11:59 -0700 Subject: [PATCH 11/24] update --- .../agent/installation/install-agent-api.md | 83 +- .../includes/nap-waf/build-nginx-image-cmd.md | 2 +- .../learn-about-deployment.md | 6 +- content/nap-waf/v4/admin-guide/install.md | 4 +- content/nap-waf/v5/admin-guide/compiler.md | 2 +- content/ngf/overview/custom-policies.md | 9 +- content/ngf/overview/product-telemetry.md | 3 +- .../load-balancer/tcp-udp-load-balancer.md | 40 +- .../load-balancer/udp-health-check.md | 160 +++- .../manage-waf-security-policies.md | 763 ++++++------------ .../overview-nap-waf-config-management.md | 72 +- 11 files changed, 519 insertions(+), 625 deletions(-) diff --git a/content/includes/agent/installation/install-agent-api.md b/content/includes/agent/installation/install-agent-api.md index 95a9650aa..15009d21f 100644 --- a/content/includes/agent/installation/install-agent-api.md +++ b/content/includes/agent/installation/install-agent-api.md @@ -1,74 +1,75 @@ -**Note**: To complete this step, make sure that `gpg` is installed on your system. You can install NGINX Agent using various command-line tools like `curl` or `wget`. If your NGINX Instance Manager host is not set up with valid TLS certificates, you can use the insecure flags provided by those tools. See the following examples: +--- +docs: DOCS-1031 +files: + - content/nim/nginx-app-protect/setup-waf-config-management.md +--- + +{{- -To create a security policy using the Instance Manager web interface: - -1. In a web browser, go to the FQDN for your NGINX Management Suite host and log in. Then, from the Launchpad menu, select **Instance Manager**. -2. On the left menu, select **App Protect**. -3. On the *Security Policies* page, select **Create**. -4. On the *Create Policy* page, fill out the necessary fields: +To create a security policy using the NGINX Instance Manager web interface: - - **Name**: Provide a name for the policy. - - **Description**: (Optional) Add a short description for the policy. - - **Enter Policy**: Type or paste the policy in JSON format into the form provided. The editor will validate the JSON for accuracy. +1. In your browser, go to the FQDN for your NGINX Instance Manager host and log in. +2. From the Launchpad menu, select **Instance Manager**. +3. In the left menu, select **App Protect**. +4. On the *Security Policies* page, select **Create**. +5. On the *Create Policy* page, enter the required information: + - **Name**: Enter a name for the policy. + - **Description**: (Optional) Add a brief description. + - **Enter Policy**: Paste or type the JSON-formatted policy into the editor. The interface automatically validates the JSON. - For more information about creating custom policies, refer to the [NGINX App Protect WAF Declarative Policy](https://docs.nginx.com/nginx-app-protect/declarative-policy/policy/) guide and the [Policy Authoring and Tuning](https://docs.nginx.com/nginx-app-protect/configuration-guide/configuration/#policy-authoring-and-tuning) section of the config guide. + For help writing custom policies, see the [NGINX App Protect WAF Declarative Policy guide](https://docs.nginx.com/nginx-app-protect/declarative-policy/policy/) and the [Policy Authoring and Tuning section](https://docs.nginx.com/nginx-app-protect/configuration-guide/configuration/#policy-authoring-and-tuning) in the configuration guide. -5. Select **Save**. +6. Select **Save**. {{%/tab%}} {{%tab name="API"%}} -To upload a new security policy, send an HTTP `POST` request to the Security Policies API endpoint. - -{{
+To upload a new security policy using the REST API, send a `POST` request to the Security Policies API endpoint. +You must encode the JSON policy using `base64`. If you send the policy in plain JSON, the request will fail. {{
-To delete a security policy using the Instance Manager web interface: +To delete a security policy using the NGINX Instance Manager web interface: + +1. In your browser, go to the FQDN for your NGINX Instance Manager host and log in. +2. From the Launchpad menu, select **Instance Manager**. +3. In the left menu, select **App Protect**. +4. On the *Security Policies* page, find the policy you want to delete. +5. Select the **Actions** menu (**...**) and choose **Delete**. -1. In a web browser, go to the FQDN for your NGINX Management Suite host and log in. Then, from the Launchpad menu, select **Instance Manager**. -2. On the left menu, select **App Protect**. -3. On the *Security Policies* page, select the **Actions** menu (represented by an ellipsis, **...**) for the policy you want to delete. Select **Delete** to remove the policy. {{%/tab%}} {{%tab name="API"%}} -To delete a security policy, send an HTTP `DELETE` request to the Security Policies API endpoint that includes the unique identifier for the policy that you want to delete. +To delete a security policy using the REST API: + +1. Retrieve the UID for the policy by sending a `GET` request to the policies endpoint: + + ```shell + curl -X GET https://{{NIM_FQDN}}/api/platform/v1/security/policies \ + -H "Authorization: Bearer
+If no time range is provided, the API defaults to showing bundles modified in the past 24 hours. {{
+You must have `"READ"` permission for the bundle to retrieve it. {{
+To upload a new security log profile, send a `POST` request to the Security Log Profiles API endpoint. +You must encode the log profile in `base64` before sending it. If you send plain JSON, the request will fail. {{
JSON Response
+{{JSON Response
+The response also contains `lastDeploymentDetails` for each instance or group. -```json -{ - "associations": [ - { - "instance": { - "hostName": "", - "systemUid": "", - "uid": "" - }, - "instanceGroup": { - "displayName": "ig1", - "instances": [ - { - "hostName": "ip-172-16-0-142", - "systemUid": "1d1f03ff-02de-32c5-8dfd-902658aada4c", - "uid": "18d074e6-3868-51ba-9999-b7466a936815" - } - ], - "lastDeploymentDetails": { - "createTime": "2023-07-05T23:01:06.679136973Z", - "details": { - "failure": [], - "pending": [], - "success": [ - { - "name": "ip-172-16-0-142" - } - ] - }, - "id": "9bfc9db7-877d-4e8e-a43d-9660a6cd11cc", - "message": "Instance Group config successfully published to ig1", - "status": "successful", - "updateTime": "2023-07-05T23:01:06.790802157Z" - }, - "uid": "0df0386e-82f7-4efc-863e-5d7cfbc3f7df" - }, - "logProfileUid": "b680f7c3-6fc0-4c6b-889a-3025580c7fcb", - "logProfileVersionDateTime": "2023-07-05T22:08:47.371Z" - }, - { - "instance": { - "hostName": "ip-172-16-0-5", - "lastDeploymentDetails": { - "createTime": "2023-07-05T21:45:08.698646791Z", - "details": { - "failure": [], - "pending": [], - "success": [ - { - "name": "ip-172-16-0-5" - } - ] - }, - "id": "73cf670a-738a-4a74-b3fb-ac9771e89814", - "message": "Instance config successfully published to", - "status": "successful", - "updateTime": "2023-07-05T21:45:08.698646791Z" - }, - "systemUid": "0afe5ac2-43aa-36c8-bcdc-7f88cdd35ab2", - "uid": "9bb4e2ef-3746-5d79-b526-e545fad27e90" - }, - "instanceGroup": { - "displayName": "", - "instances": [], - "uid": "" - }, - "logProfileUid": "bb3badb2-f8f5-4b95-9428-877fc208e2f1", - "logProfileVersionDateTime": "2023-07-03T21:46:17.006Z" - } - ] -} -``` +### Check status for a specific instance -JSON Response
+In the response, look for the `lastDeploymentDetails` field, which shows the deployment status and any related errors. -```json -{ - "build": { - "nginxPlus": true, - "release": "nginx-plus-r28", - "version": "1.23.2" - }, - "configPath": "/etc/nginx/nginx.conf", - "configVersion": { - "instanceGroup": { - "createTime": "0001-01-01T00:00:00Z", - "uid": "", - "versionHash": "" - }, - "versions": [ - { - "createTime": "2023-01-14T10:48:46.319Z", - "uid": "5663cf4e-a0c7-50c8-b93c-16fd11a0f00b", - "versionHash": "922e9d40fa6d4dd3a4b721295b8ecd95f73402644cb8d234f9f4f862b8a56bfc" - } - ] - }, - "displayName": "ip-192-0-2-27", - "links": [ - { - "rel": "/api/platform/v1/systems/b9df6377-2c4f-3266-a64a-e064b0371c73", - "name": "system" - }, - { - "rel": "/api/platform/v1/systems/b9df6377-2c4f-3266-a64a-e064b0371c73/instances/5663cf4e-a0c7-50c8-b93c-16fd11a0f00b", - "name": "self" - }, - { - "rel": "/api/platform/v1/systems/instances/deployments/b31c6ab1-4a46-4c81-a065-204575145e8e", - "name": "deployment" - } - ], - "processPath": "/usr/sbin/nginx", - "registrationTime": "2023-01-14T10:12:31.000Z", - "startTime": "2023-01-14T10:09:43Z", - "status": { - "lastStatusReport": "2023-01-14T11:11:49.323495017Z", - "state": "online" - }, - "uid": "5663cf4e-a0c7-50c8-b93c-16fd11a0f00b", - "version": "1.23.2", - "appProtect": { - "attackSignatureVersion": "Available after publishing Attack Signatures from Instance Manager", - "status": "active", - "threatCampaignVersion": "Available after publishing Threat Campaigns from Instance Manager", - "version": "4.2.0" - }, - "configureArgs": [ - ... - ], - "lastDeploymentDetails": { - "createTime": "2023-01-14T11:10:25.096812852Z", - "details": { - "error": "{\"instance:b9df6377-2c4f-3266-a64a-e064b0371c73\":\"failed building config payload: policy compilation failed for deployment b31c6ab1-4a46-4c81-a065-204575145e8e due to integrations service error: the specified compiler (4.2.0) is missing, please install it and try again.\"}", - "failure": [ - { - "failMessage": "failed building config payload: policy compilation failed for deployment b31c6ab1-4a46-4c81-a065-204575145e8e due to integrations service error: the specified compiler (4.2.0) is missing, please install it and try again.", - "name": "ip-192-0-2-27" - } - ], - "pending": [], - "success": [] - }, - "id": "b31c6ab1-4a46-4c81-a065-204575145e8e", - "message": "Instance config failed to publish to", - "status": "failed", - "updateTime": "2023-01-14T11:10:25.175145693Z" - }, - "loadableModules": [ - ... - ], - "packages": [ - ... - ], - "processId": "10345", - "ssl": { - "built": null, - "runtime": null - } -} -``` +### Check deployment result by deployment ID -JSON Response
- -```json -{ - "createTime": "2023-01-14T04:35:47.566082799Z", - "details": { - "error": "{\"instance:8a2092aa-5612-370d-bff0-5d7521e206d6\":\"failed building config payload: policy bundle compilation failed for d38a8e5d-2312-4046-a60f-a30a4aea1fbb, integrations service returned the following error: missing the specified compiler (4.2.0) please install it and try again\"}", - "failure": [ - { - "failMessage": "failed building config payload: policy bundle compilation failed for d38a8e5d-2312-4046-a60f-a30a4aea1fbb, integrations service returned the following error: missing the specified compiler (4.2.0) please install it and try again", - "name": "ip-192-0-2-243" - } - ], - "pending": [], - "success": [] - }, - "id": "d38a8e5d-2312-4046-a60f-a30a4aea1fbb", - "message": "Instance config failed to publish to", - "status": "failed", - "updateTime": "2023-01-14T04:35:47.566082799Z" -} -``` - -Keep an inventory of your deployments
>>>>>>> 09d8a53f (More) {{ end }} +<<<<<<< HEAD {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Organize users with RBAC")}}Assign responsibilities with role-based access control
+======= + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Monitor your certificates")}} +Detect and resolve expired SSL certs in minutes
+>>>>>>> 5e6d32b4 (new messages) {{ end }} <<<<<<< HEAD {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Automate with the NGINX One API")}} @@ -62,11 +67,15 @@Secure your systems with role-based access control
{{ end }} {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Change multiple instances with one push")}} -Configure and synchronize groups of NGINX instances simultaneously
+Synchronize changes across cloud environments
{{ end }} {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "NGINX One API")}} +<<<<<<< HEADAutomate NGINX fleet management
>>>>>>> 09d8a53f (More) +======= +Automate NGINX fleet management from the CLI
+>>>>>>> 5e6d32b4 (new messages) {{ end }} {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Glossary")}}Learn terms unique to NGINX One Console
From 43ef45c8127b203b5a286fd05b1a23264355c056 Mon Sep 17 00:00:00 2001 From: Mike Jang <3287976+mjang@users.noreply.github.com> Date: Thu, 15 May 2025 09:48:37 -0700 Subject: [PATCH 13/24] Sync with presentation --- content/nginx-one/secure-your-fleet/_index.md | 6 ++++++ layouts/partials/list-main.html | 16 ++++++++++++++-- 2 files changed, 20 insertions(+), 2 deletions(-) create mode 100644 content/nginx-one/secure-your-fleet/_index.md diff --git a/content/nginx-one/secure-your-fleet/_index.md b/content/nginx-one/secure-your-fleet/_index.md new file mode 100644 index 000000000..3d693a250 --- /dev/null +++ b/content/nginx-one/secure-your-fleet/_index.md @@ -0,0 +1,6 @@ +--- +title: Secure your fleet +description: +weight: 250 +url: /nginx-one/secure-your-fleet +--- diff --git a/layouts/partials/list-main.html b/layouts/partials/list-main.html index 3dd81da99..381678a1c 100644 --- a/layouts/partials/list-main.html +++ b/layouts/partials/list-main.html @@ -19,7 +19,7 @@
- {{ if or (lt .WordCount 1) (eq $PageTitle "F5 NGINX One Console") (eq $PageTitle "F5 NGINX App Protect DoS") (eq $PageTitle "F5 NGINX Plus") }}
+ {{ if or (lt .WordCount 1) (eq $PageTitle "fF5 NGINX One Console") (eq $PageTitle "F5 NGINX App Protect DoS") (eq $PageTitle "F5 NGINX Plus") }}
@@ -37,8 +37,16 @@
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Get started")}}
See benefits from the NGINX One Console
{{ end }}
+<<<<<<< HEAD
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Draft new configurations")}}
Work with Staged Configurations
+=======
+ {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Set up new instances")}}
+ Collaborate with Staged Configurations
+ {{ end }}
+ {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Secure your fleet")}}
+ Configure alerts that match your security policies
+>>>>>>> 3dbfb304 (Sync with presentation)
{{ end }}
<<<<<<< HEAD
+>>>>>>> 42d749df (Make more prod ready)
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Watch your NGINX instances")}}
Keep an inventory of your deployments
>>>>>>> 09d8a53f (More)
From 7254b72c81a96fd5657e9aa29d1c97de72a2c4cd Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Thu, 22 May 2025 11:15:19 -0700
Subject: [PATCH 16/24] More
---
.../includes/nginx-one/how-to/add-instance.md | 3 ++
.../nginx-one/nginx-configs/add-instance.md | 30 +++----------
layouts/partials/list-main.html | 43 +------------------
3 files changed, 10 insertions(+), 66 deletions(-)
diff --git a/content/includes/nginx-one/how-to/add-instance.md b/content/includes/nginx-one/how-to/add-instance.md
index 94f0b628b..b9c5c86b8 100644
--- a/content/includes/nginx-one/how-to/add-instance.md
+++ b/content/includes/nginx-one/how-to/add-instance.md
@@ -1,8 +1,11 @@
---
docs:
+<<<<<<< HEAD
files:
- content/nginx-one/connect-instances/add-instance.md
- content/nginx-one/getting-started.md
+=======
+>>>>>>> 4067237f (More)
---
You can add an instance to NGINX One Console in the following ways:
diff --git a/content/nginx-one/nginx-configs/add-instance.md b/content/nginx-one/nginx-configs/add-instance.md
index ddf5eb095..fd3b70fd5 100644
--- a/content/nginx-one/nginx-configs/add-instance.md
+++ b/content/nginx-one/nginx-configs/add-instance.md
@@ -16,34 +16,16 @@ to set up a data plane key to connect your instances to NGINX One.
Before you add an instance to NGINX One Console, ensure:
-- You have administrator access to NGINX One Console.
-- You have configured instances of NGINX that you want to manage through NGINX One Console.
-- You have or are ready to configure a data plane key.
-- You have or are ready to set up managed certificates.
+- You have [administrator access]({{< ref "/nginx-one/rbac/roles.md" >}}) to NGINX One Console.
+- You have [configured instances of NGINX]({{< ref "/nginx-one/getting-started.md#add-your-nginx-instances-to-nginx-one" >}}) that you want to manage through NGINX One Console.
+- You have or are ready to configure a [data plane key]({{< ref "/nginx-one/getting-started.md#generate-data-plane-key" >}}).
+- You have or are ready to set up [managed certificates]({{< ref "/nginx-one/certificates/manage-certificates.md" >}}).
{{< note >}}If this is the first time an instance is being added to a Config Sync Group, and you have not yet defined the configuration for that Config Sync Group, that instance provides the template for that group. For more information, see [Configuration management]({{< ref "nginx-one/config-sync-groups/manage-config-sync-groups#configuration-management" >}}).{{< /note >}}
## Add an instance
-You can add an instance to NGINX One Console in the following ways:
-
-- Directly, under **Instances**
-- Indirectly, by selecting a Config Sync Group, and selecting **Add Instance to Config Sync Group**
-
-In either case, NGINX One Console gives you a choice for data plane keys:
-
-- Create a new key
-- Use an existing key
-
-NGINX One Console takes the option you use, and adds the data plane key to a command that you'd use to register your target instance. You should see the command in the **Add Instance** screen in the console.
-
-Connect to the host where your NGINX instance is running. Run the provided command to [install NGINX Agent]({{< ref "/nginx-one/getting-started#install-nginx-agent" >}}) dependencies and packages on that host.
-
-```bash
-curl https://agent.connect.nginx.com/nginx-agent/install | DATA_PLANE_KEY="" sh -s -- -y
-```
-
-Once the process is complete, you can configure that instance in your NGINX One Console.
+{{< include "/nginx-one/how-to/add-instance.md" >}}
## Managed and Unmanaged Certificates
@@ -51,7 +33,7 @@ If you add an instance with SSL/TLS certificates, those certificates can match a
### If the certificate is already managed
-If you add an instance with a managed certificate, as described in [Add your NGINX instances to NGINX One], these certificates are added to your list of **Managed Certificates**.
+If you add an instance with a managed certificate, as described in [Add your NGINX instances to NGINX One]({{< ref "/nginx-one/getting-started.md#add-your-nginx-instances-to-nginx-one" >}}), these certificates are added to your list of **Managed Certificates**.
NGINX One Console can manage your instances along with those certificates.
diff --git a/layouts/partials/list-main.html b/layouts/partials/list-main.html
index 6cb957c27..be455babf 100644
--- a/layouts/partials/list-main.html
+++ b/layouts/partials/list-main.html
@@ -19,7 +19,7 @@
- {{ if or (lt .WordCount 1) (eq $PageTitle "fF5 NGINX One Console") (eq $PageTitle "F5 NGINX App Protect DoS") (eq $PageTitle "F5 NGINX Plus") }}
+ {{ if or (lt .WordCount 1) (eq $PageTitle "F5 NGINX One Console") (eq $PageTitle "F5 NGINX App Protect DoS") (eq $PageTitle "F5 NGINX Plus") }}
@@ -37,61 +37,20 @@
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Get started")}}
See benefits from the NGINX One Console
{{ end }}
-<<<<<<< HEAD
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Draft new configurations")}}
Work with Staged Configurations
-=======
- {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Set up new instances")}}
- Collaborate with Staged Configurations
{{ end }}
-
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Manage your NGINX instances")}}
Monitor and maintain your deployments
-=======
-=======
- {{ end }} -->
->>>>>>> 42d749df (Make more prod ready)
- {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Watch your NGINX instances")}}
- Keep an inventory of your deployments
->>>>>>> 09d8a53f (More)
{{ end }}
-<<<<<<< HEAD
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Organize users with RBAC")}}
Assign responsibilities with role-based access control
-=======
- {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Monitor your certificates")}}
-<<<<<<< HEAD
- Detect and resolve expired SSL certs in minutes
->>>>>>> 5e6d32b4 (new messages)
-=======
- Update your SSL certs before they expire
->>>>>>> 3dbfb304 (Sync with presentation)
{{ end }}
-<<<<<<< HEAD
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Automate with the NGINX One API")}}
Manage your NGINX fleet over REST
-=======
- {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Organize your administrators with RBAC")}}
- Secure your systems with role-based access control
- {{ end }}
- {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Change multiple instances with one push")}}
- Simplify changes with Config Sync Groups
- {{ end }}
- {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "NGINX One API")}}
-<<<<<<< HEAD
- Automate NGINX fleet management
->>>>>>> 09d8a53f (More)
-=======
- Automate NGINX fleet management from the CLI
->>>>>>> 5e6d32b4 (new messages)
{{ end }}
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Glossary")}}
Learn terms unique to NGINX One Console
From 245683258ebeeb4f14be9808f0c6045c00277da0 Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Thu, 22 May 2025 11:48:39 -0700
Subject: [PATCH 17/24] more
---
content/nginx-one/api/_index.md | 4 +
content/nginx-one/nginx-configs/_index.md | 4 +
.../manage-config-sync-groups.md | 239 ------------------
content/nginx-one/staged-configs/_index.md | 4 +
4 files changed, 12 insertions(+), 239 deletions(-)
delete mode 100644 content/nginx-one/nginx-configs/manage-config-sync-groups.md
diff --git a/content/nginx-one/api/_index.md b/content/nginx-one/api/_index.md
index 1735740f8..b74c67e09 100644
--- a/content/nginx-one/api/_index.md
+++ b/content/nginx-one/api/_index.md
@@ -1,9 +1,13 @@
---
<<<<<<< HEAD
+<<<<<<< HEAD
title: Automate with the NGINX One API
=======
title: NGINX One API
>>>>>>> c7ce27ce (Draft: new N1C doc homepage)
+=======
+title: Automation with the NGINX One API
+>>>>>>> 614bafed (more)
description:
weight: 700
url: /nginx-one/api
diff --git a/content/nginx-one/nginx-configs/_index.md b/content/nginx-one/nginx-configs/_index.md
index 18ece7e11..4b732ef6e 100644
--- a/content/nginx-one/nginx-configs/_index.md
+++ b/content/nginx-one/nginx-configs/_index.md
@@ -2,6 +2,7 @@
description:
<<<<<<< HEAD
<<<<<<< HEAD
+<<<<<<< HEAD
title: Manage your NGINX instances
=======
title: Organize your NGINX instances
@@ -9,6 +10,9 @@ title: Organize your NGINX instances
=======
title: Watch your NGINX instances
>>>>>>> 09d8a53f (More)
+=======
+title: Access and connect to your NGINX instances
+>>>>>>> 614bafed (more)
weight: 300
url: /nginx-one/nginx-configs
---
diff --git a/content/nginx-one/nginx-configs/manage-config-sync-groups.md b/content/nginx-one/nginx-configs/manage-config-sync-groups.md
deleted file mode 100644
index 41589dadd..000000000
--- a/content/nginx-one/nginx-configs/manage-config-sync-groups.md
+++ /dev/null
@@ -1,239 +0,0 @@
----
-docs: null
-title: Manage config sync groups
-toc: true
-weight: 300
-type:
-- how-to
----
-
-## Overview
-
-This guide explains how to create and manage config sync groups in the F5 NGINX One Console. Config sync groups synchronize NGINX configurations across multiple NGINX instances, ensuring consistency and ease of management.
-
-If you’ve used [instance groups in NGINX Instance Manager]({{< ref "/nim/nginx-instances/manage-instance-groups.md" >}}), you’ll find config sync groups in NGINX One similar, though the steps and terminology differ slightly.
-
-## Before you start
-
-Before you create and manage config sync groups, ensure:
-
-- You have access to the NGINX One Console.
-- You have the necessary permissions to create and manage config sync groups.
-- NGINX instances are properly registered with NGINX One if you plan to add existing instances to a config sync group.
-
-## Important considerations
-
-- **NGINX Agent configuration file location**: When you run the NGINX Agent installation script to register an instance with NGINX One, the script creates the `agent-dynamic.conf` file, which contains settings for the NGINX Agent, including the specified config sync group. This file is typically located in `/var/lib/nginx-agent/` on most systems; however, on FreeBSD, it's located at `/var/db/nginx-agent/`.
-
-- **Mixing NGINX Open Source and NGINX Plus instances**: You can add both NGINX Open Source and NGINX Plus instances to the same config sync group, but there are limitations. If your configuration includes features exclusive to NGINX Plus, synchronization will fail on NGINX Open Source instances because they don't support these features. NGINX One allows you to mix NGINX instance types for flexibility, but it’s important to ensure that the configurations you're applying are compatible with all instances in the group.
-
-- **Single config sync group membership**: An instance can join only one config sync group at a time.
-
-- **Configuration inheritance**: If the config sync group already has a configuration defined, that configuration will be pushed to instances when they join.
-
-- **Using an instance's configuration for the group configuration**: If an instance is the first to join a config sync group and the group's configuration hasn't been defined, the instance’s configuration will become the group’s configuration. Any instances added later will automatically inherit this configuration.
-
- {{< note >}} If you add multiple instances to a single config sync group, simultaneously (with automation), follow these steps. Your instances will inherit your desired configuration:
-
- 1. Create a config sync group.
- 1. Add a configuration to the config sync group, so all instances inherit it.
- 1. Add the instances in a separate operation.
-
- Your instances should synchronize with your desired configuration within 30 seconds. {{< /note >}}
-
-- **Persistence of a config sync group's configuration**: The configuration for a config sync group persists until you delete the group. Even if you remove all instances, the group's configuration stays intact. Any new instances that join later will automatically inherit this configuration.
-
-- **Config sync groups vs. cluster syncing**: Config sync groups are not the same as cluster syncing. Config sync groups let you to manage and synchronize configurations across multiple NGINX instances as a single entity. This is particularly useful when your NGINX instances are load-balanced by an external load balancer, as it ensures consistency across all instances. In contrast, cluster syncing, like [zone syncing]({{< ref "nginx/admin-guide/high-availability/zone_sync_details.md" >}}), ensures data consistency and high availability across NGINX instances in a cluster. While config sync groups focus on configuration management, cluster syncing supports failover and data consistency.
-
-## Create a config sync group
-
-Creating a config sync group allows you to manage the configurations of multiple NGINX instances as a single entity.
-
-1. On the left menu, select **Config Sync Groups**.
-2. Select **Add Config Sync Group**.
-3. In the **Name** field, type a name for your config sync group.
-4. Select **Create** to add the config sync group.
-
-## Manage config sync group membership
-
-### Add an existing instance to a config sync group {#add-an-existing-instance-to-a-config-sync-group}
-
-You can add existing NGINX instances that are already registered with NGINX One to a config sync group.
-
-1. Open a command-line terminal on the NGINX instance.
-2. Open the `/var/lib/nginx-agent/agent-dynamic.conf` file in a text editor.
-3. At the end of the file, add a new line beginning with `instance_group:`, followed by the config sync group name.
-
- ``` text
- instance_group:
- ```
-
-4. Restart NGINX Agent:
-
- ``` shell
- sudo systemctl restart nginx-agent
- ```
-
-### Add a new instance to a config sync group {#add-a-new-instance-to-a-config-sync-group}
-
-When adding a new NGINX instance that is not yet registered with NGINX One, you need a data plane key to securely connect the instance. You can generate a new data plane key during the process or use an existing one if you already have it.
-
-1. On the left menu, select **Config Sync Groups**.
-2. Select the config sync group in the list.
-3. In the **Instances** pane, select **Add Instance to Config Sync Group**.
-4. In the **Add Instance to Config Sync Group** dialog, select **Register a new instance with NGINX One then add to config sync group**.
-5. Select **Next**.
-6. **Generate a new data plane key** (choose this option if you don't have an existing key):
-
- - Select **Generate new key** to create a new data plane key for the instance.
- - Select **Generate Data Plane Key**.
- - Copy and securely store the generated key, as it is displayed only once.
-
-7. **Use an existing data plane key** (choose this option if you already have a key):
-
- - Select **Use existing key**.
- - In the **Data Plane Key** field, enter the existing data plane key.
-
-{{}}
-
-{{%tab name="Virtual Machine or Bare Metal"%}}
-
-8. Run the provided command, which includes the data plane key, in your NGINX instance terminal to register the instance with NGINX One.
-9. Select **Done** to complete the process.
-
-{{%/tab%}}
-
-{{%tab name="Docker Container"%}}
-
-8. **Log in to the NGINX private registry**:
-
- - Replace `YOUR_JWT_HERE` with your JSON Web Token (JWT) from [MyF5](https://my.f5.com/manage/s/).
-
- ```shell
- sudo docker login private-registry.nginx.com --username=YOUR_JWT_HERE --password=none
- ```
-
-9. **Pull the Docker image**:
-
- - From the **OS Type** list, choose the appropriate operating system for your Docker image.
- - After selecting the OS, run the provided command to pull the Docker image.
-
- **Note**: Subject to availability, you can modify the `agent: ` to match the specific NGINX Plus version, OS type, and OS version you need. For example, you might use `agent: r32-ubi-9`. For more details on version tags and how to pull an image, see [Deploying NGINX and NGINX Plus on Docker]({{< ref "nginx/admin-guide/installing-nginx/installing-nginx-docker.md#pulling-the-image" >}}).
-
-10. Run the provided command, which includes the data plane key, in your NGINX instance terminal to start the Docker container.
-
-11. Select **Done** to complete the process.
-
-{{%/tab%}}
-
-{{ }}
-
-{{}}
-
-Data plane keys are required for registering NGINX instances with the NGINX One Console. These keys serve as secure tokens, ensuring that only authorized instances can connect and communicate with NGINX One.
-
-For more details on creating and managing data plane keys, see [Create and manage data plane keys]({{}}).
-
-{{ }}
-
-### Change the config sync group for an instance
-
-If you need to move an NGINX instance to a different config sync group, follow these steps:
-
-1. Open a command-line terminal on the NGINX instance.
-2. Open the `/var/lib/nginx-agent/agent-dynamic.conf` file in a text editor.
-3. Locate the line that begins with `instance_group:` and change it to the name of the new config sync group.
-
- ``` text
- instance_group:
- ```
-
-4. Restart NGINX Agent by running the following command:
-
- ```shell
- sudo systemctl restart nginx-agent
- ```
-
-**Important:** If the instance is the first to join the new config sync group and a group configuration hasn’t been added manually beforehand, the instance’s configuration will automatically become the group’s configuration. Any instances added to this group later will inherit this configuration.
-
-### Remove an instance from a config sync group
-
-If you need to remove an NGINX instance from a config sync group without adding it to another group, follow these steps:
-
-1. Open a command-line terminal on the NGINX instance.
-2. Open the `/var/lib/nginx-agent/agent-dynamic.conf` file in a text editor.
-3. Locate the line that begins with `instance_group:` and either remove it or comment it out by adding a `#` at the beginning of the line.
-
- ```text
- # instance_group:
- ```
-
-4. Restart NGINX Agent:
-
- ```shell
- sudo systemctl restart nginx-agent
- ```
-
-By removing or commenting out this line, the instance will no longer be associated with any config sync group.
-
-## Add the config sync group configuration
-
-You can set the configuration for a config sync group in two ways:
-
-### Define the group configuration manually
-
-You can manually define the group's configuration before adding any instances. When you add instances to the group later, they automatically inherit this configuration.
-
-To manually set the group configuration:
-
-1. Follow steps 1–4 in the [**Create a config sync group**](#create-a-config-sync-group) section to create your config sync group.
-2. After creating the group, select the **Configuration** tab.
-3. Since no instances have been added, the **Configuration** tab will show an empty configuration with a message indicating that no config files exist yet.
-4. To add a configuration, select **Edit Configuration**.
-5. In the editor, define your NGINX configuration as needed. This might include adding or modifying `nginx.conf` or other related files.
-6. After making your changes, select **Next** to view a split screen showing your changes.
-7. If you're satisfied with the configuration, select **Save and Publish**.
-
-### Use an instance's configuration
-
-If you don't manually define a group config, the NGINX configuration of the first instance added to a config sync group becomes the group's configuration. Any additional instances added afterward inherit this group configuration.
-
-To set the group configuration by adding an instance:
-
-1. Follow the steps in the [**Add an existing instance to a config sync group**](#add-an-existing-instance-to-a-config-sync-group) or [**Add a new instance to a config sync group**](#add-a-new-instance-to-a-config-sync-group) sections to add your first instance to the group.
-2. The NGINX configuration from this instance will automatically become the group's configuration.
-3. You can further edit and publish this configuration by following the steps in the [**Publish the config sync group configuration**](#publish-the-config-sync-group-configuration) section.
-
-## Publish the config sync group configuration {#publish-the-config-sync-group-configuration}
-
-After the config sync group is created, you can modify and publish the group's configuration as needed. Any changes made to the group configuration will be applied to all instances within the group.
-
-1. On the left menu, select **Config Sync Groups**.
-2. Select the config sync group in the list.
-3. Select the **Configuration** tab to view the group's NGINX configuration.
-4. To modify the group's configuration, select **Edit Configuration**.
-5. Make the necessary changes to the configuration.
-6. When you're finished, select **Next**. A split view displays the changes.
-7. If you're satisfied with the changes, select **Save and Publish**.
-
-Publishing the group configuration ensures that all instances within the config sync group are synchronized with the latest group configuration. This helps maintain consistency across all instances in the group, preventing configuration drift.
-
-## Understanding config sync statuses
-
-The **Config Sync Status** column on the **Config Sync Groups** page provides insight into the synchronization state of your NGINX instances within each group.
-
-{{}}
-| **Status** | **Description** |
-|-----------------------|------------------------------------------------------------------------------------------------------------------------------------------------------|
-| **In Sync** | All instances within the config sync group have configurations that match the group configuration. No action is required. |
-| **Out of Sync** | At least one instance in the group has a configuration that differs from the group's configuration. You may need to review and resolve discrepancies to ensure consistency. |
-| **Sync in Progress** | An instance is currently being synchronized with the group's configuration. This status appears when an instance is moved to a new group or when a configuration is being applied. |
-| **Unknown** | The synchronization status of the instances in this group cannot be determined. This could be due to connectivity issues, instances being offline, or other factors. Investigating the cause of this status is recommended. |
-{{ }}
-
-Monitoring the **Config Sync Status** helps ensure that your configurations are consistently applied across all instances in a group, reducing the risk of configuration drift.
-
-## See also
-
-- [Create and manage data plane keys]({{< ref "/nginx-one/how-to/data-plane-keys/create-manage-data-plane-keys.md" >}})
-- [View and edit NGINX configurations]({{< ref "/nginx-one/nginx-configs/view-edit-nginx-configurations.md" >}})
diff --git a/content/nginx-one/staged-configs/_index.md b/content/nginx-one/staged-configs/_index.md
index 66cf13915..b6cb02bae 100644
--- a/content/nginx-one/staged-configs/_index.md
+++ b/content/nginx-one/staged-configs/_index.md
@@ -1,11 +1,15 @@
---
description:
<<<<<<< HEAD
+<<<<<<< HEAD
title: Draft new configurations
weight: 400
url: /nginx-one/staged-configs
=======
title: Set up new instances
+=======
+title: Draft new instances
+>>>>>>> 614bafed (more)
weight: 200
url: /nginx-one/how-to/staged-configs
>>>>>>> c7ce27ce (Draft: new N1C doc homepage)
From 662a65ec690fc62bdb3ce7b225f5f65bcda1fa33 Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Thu, 22 May 2025 12:34:50 -0700
Subject: [PATCH 18/24] based on Jason's feedback
---
content/nginx-one/api/_index.md | 4 ++++
content/nginx-one/certificates/manage-certificates.md | 2 +-
content/nginx-one/config-sync-groups/add-file-csg.md | 2 +-
.../config-sync-groups/manage-config-sync-groups.md | 2 +-
content/nginx-one/nginx-configs/_index.md | 4 ++++
content/nginx-one/nginx-configs/add-file.md | 2 +-
.../nginx-configs/view-edit-nginx-configurations.md | 8 ++++++++
content/nginx-one/rbac/_index.md | 4 ++++
content/nginx-one/staged-configs/_index.md | 4 ++++
9 files changed, 28 insertions(+), 4 deletions(-)
diff --git a/content/nginx-one/api/_index.md b/content/nginx-one/api/_index.md
index b74c67e09..5372d8f12 100644
--- a/content/nginx-one/api/_index.md
+++ b/content/nginx-one/api/_index.md
@@ -1,6 +1,7 @@
---
<<<<<<< HEAD
<<<<<<< HEAD
+<<<<<<< HEAD
title: Automate with the NGINX One API
=======
title: NGINX One API
@@ -8,6 +9,9 @@ title: NGINX One API
=======
title: Automation with the NGINX One API
>>>>>>> 614bafed (more)
+=======
+title: Automate with the NGINX One API
+>>>>>>> 4da8aa7e (based on Jason's feedback)
description:
weight: 700
url: /nginx-one/api
diff --git a/content/nginx-one/certificates/manage-certificates.md b/content/nginx-one/certificates/manage-certificates.md
index 13c532e38..136a4e299 100644
--- a/content/nginx-one/certificates/manage-certificates.md
+++ b/content/nginx-one/certificates/manage-certificates.md
@@ -193,5 +193,5 @@ To convert these cerificates to managed, start with the Certificates menu, and s
## See also
- [Create and manage data plane keys]({{< ref "/nginx-one/how-to/data-plane-keys/create-manage-data-plane-keys.md" >}})
-- [View and edit NGINX configurations]({{< ref "/nginx-one/nginx-configs/view-edit-nginx-configurations.md" >}})
+- [Add an instance]({{< ref "/nginx-one/nginx-configs/add-instance.md" >}})
- [Add a file in a configuration]({{< ref "/nginx-one/nginx-configs/add-file.md" >}})
diff --git a/content/nginx-one/config-sync-groups/add-file-csg.md b/content/nginx-one/config-sync-groups/add-file-csg.md
index 9b6905aea..c416848a8 100644
--- a/content/nginx-one/config-sync-groups/add-file-csg.md
+++ b/content/nginx-one/config-sync-groups/add-file-csg.md
@@ -63,5 +63,5 @@ With this option, You can incorporate [Managed certificates]({{< ref "/nginx-one
## See also
- [Create and manage data plane keys]({{< ref "/nginx-one/how-to/data-plane-keys/create-manage-data-plane-keys.md" >}})
-- [View and edit NGINX configurations]({{< ref "/nginx-one/nginx-configs/view-edit-nginx-configurations.md" >}})
+- [Add an NGINX instance]({{< ref "/nginx-one/nginx-configs/add-instance.md" >}})
- [Manage certificates]({{< ref "/nginx-one/certificates/manage-certificates.md" >}})
diff --git a/content/nginx-one/config-sync-groups/manage-config-sync-groups.md b/content/nginx-one/config-sync-groups/manage-config-sync-groups.md
index 8b24001cd..056414a67 100644
--- a/content/nginx-one/config-sync-groups/manage-config-sync-groups.md
+++ b/content/nginx-one/config-sync-groups/manage-config-sync-groups.md
@@ -258,4 +258,4 @@ Monitor the **Config Sync Status** column. It can help you ensure that your conf
## See also
- [Create and manage data plane keys]({{< ref "/nginx-one/how-to/data-plane-keys/create-manage-data-plane-keys.md" >}})
-- [View and edit NGINX configurations]({{< ref "/nginx-one/nginx-configs/view-edit-nginx-configurations.md" >}})
+- [Add an NGINX instance]({{< ref "/nginx-one/nginx-configs/add-instance.md" >}})
diff --git a/content/nginx-one/nginx-configs/_index.md b/content/nginx-one/nginx-configs/_index.md
index 4b732ef6e..3dcf3860b 100644
--- a/content/nginx-one/nginx-configs/_index.md
+++ b/content/nginx-one/nginx-configs/_index.md
@@ -3,6 +3,7 @@ description:
<<<<<<< HEAD
<<<<<<< HEAD
<<<<<<< HEAD
+<<<<<<< HEAD
title: Manage your NGINX instances
=======
title: Organize your NGINX instances
@@ -13,6 +14,9 @@ title: Watch your NGINX instances
=======
title: Access and connect to your NGINX instances
>>>>>>> 614bafed (more)
+=======
+title: Manage your NGINX instances
+>>>>>>> 4da8aa7e (based on Jason's feedback)
weight: 300
url: /nginx-one/nginx-configs
---
diff --git a/content/nginx-one/nginx-configs/add-file.md b/content/nginx-one/nginx-configs/add-file.md
index 15e301e57..0f7570ba6 100644
--- a/content/nginx-one/nginx-configs/add-file.md
+++ b/content/nginx-one/nginx-configs/add-file.md
@@ -76,6 +76,6 @@ Enter the name of the desired configuration file, such as `abc.conf` and select
- [Manage certificates]({{< ref "/nginx-one/nginx-configs/certificates/manage-certificates.md" >}})
=======
- [Create and manage data plane keys]({{< ref "/nginx-one/how-to/data-plane-keys/create-manage-data-plane-keys.md" >}})
-- [View and edit NGINX configurations]({{< ref "/nginx-one/nginx-configs/view-edit-nginx-configurations.md" >}})
+- [Add an NGINX instance]({{< ref "/nginx-one/nginx-configs/add-instance.md" >}})
- [Manage certificates]({{< ref "/nginx-one/certificates/manage-certificates.md" >}})
>>>>>>> c7ce27ce (Draft: new N1C doc homepage)
diff --git a/content/nginx-one/nginx-configs/view-edit-nginx-configurations.md b/content/nginx-one/nginx-configs/view-edit-nginx-configurations.md
index 91b37552d..074dbdbaa 100644
--- a/content/nginx-one/nginx-configs/view-edit-nginx-configurations.md
+++ b/content/nginx-one/nginx-configs/view-edit-nginx-configurations.md
@@ -1,11 +1,15 @@
---
# We use sentence case and present imperative tone
<<<<<<< HEAD
+<<<<<<< HEAD
title: View and edit an NGINX instance
# Weights are assigned in increments of 100: determines sorting order
weight: 200
=======
title: View and edit NGINX configurations
+=======
+title: View and edit an NGINX instance
+>>>>>>> 4da8aa7e (based on Jason's feedback)
# Weights are assigned in increments of 100: determines sorting order
weight: 300
>>>>>>> c7ce27ce (Draft: new N1C doc homepage)
@@ -18,6 +22,7 @@ product: NGINX One
---
+<<<<<<< HEAD
<<<<<<< HEAD
This guide explains how to edit the configuration of an existing **Instance** in your NGINX One Console.
=======
@@ -33,6 +38,9 @@ Before you add **Instances** to NGINX One Console, ensure:
Once you've registered your NGINX Instances with the F5 NGINX One Console, you can view and edit their NGINX configurations on the **Instances** details page.
>>>>>>> c7ce27ce (Draft: new N1C doc homepage)
+=======
+This guide explains how to edit the configuration of an existing **Instance** in your NGINX One Console.
+>>>>>>> 4da8aa7e (based on Jason's feedback)
To view and edit an NGINX configuration, follow these steps:
diff --git a/content/nginx-one/rbac/_index.md b/content/nginx-one/rbac/_index.md
index 4e50aa4ca..cac8d28a1 100644
--- a/content/nginx-one/rbac/_index.md
+++ b/content/nginx-one/rbac/_index.md
@@ -1,10 +1,14 @@
---
<<<<<<< HEAD
+<<<<<<< HEAD
title: Organize users with RBAC
description:
weight: 600
=======
title: Organize your administrators with RBAC
+=======
+title: Organize administrators with RBAC
+>>>>>>> 4da8aa7e (based on Jason's feedback)
description:
weight: 500
>>>>>>> c7ce27ce (Draft: new N1C doc homepage)
diff --git a/content/nginx-one/staged-configs/_index.md b/content/nginx-one/staged-configs/_index.md
index b6cb02bae..848874c60 100644
--- a/content/nginx-one/staged-configs/_index.md
+++ b/content/nginx-one/staged-configs/_index.md
@@ -2,6 +2,7 @@
description:
<<<<<<< HEAD
<<<<<<< HEAD
+<<<<<<< HEAD
title: Draft new configurations
weight: 400
url: /nginx-one/staged-configs
@@ -10,6 +11,9 @@ title: Set up new instances
=======
title: Draft new instances
>>>>>>> 614bafed (more)
+=======
+title: Draft new instances (Staged Configuration)
+>>>>>>> 4da8aa7e (based on Jason's feedback)
weight: 200
url: /nginx-one/how-to/staged-configs
>>>>>>> c7ce27ce (Draft: new N1C doc homepage)
From ae8e34abab6488506c4af9b808a4b8ac07a4cb02 Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Fri, 23 May 2025 12:21:45 -0700
Subject: [PATCH 19/24] More
---
content/nginx-one/nginx-configs/_index.md | 4 ++++
1 file changed, 4 insertions(+)
diff --git a/content/nginx-one/nginx-configs/_index.md b/content/nginx-one/nginx-configs/_index.md
index 3dcf3860b..5cf29aa32 100644
--- a/content/nginx-one/nginx-configs/_index.md
+++ b/content/nginx-one/nginx-configs/_index.md
@@ -4,6 +4,7 @@ description:
<<<<<<< HEAD
<<<<<<< HEAD
<<<<<<< HEAD
+<<<<<<< HEAD
title: Manage your NGINX instances
=======
title: Organize your NGINX instances
@@ -17,6 +18,9 @@ title: Access and connect to your NGINX instances
=======
title: Manage your NGINX instances
>>>>>>> 4da8aa7e (based on Jason's feedback)
+=======
+title: Add and manage your NGINX instances
+>>>>>>> f6a622d3 (More)
weight: 300
url: /nginx-one/nginx-configs
---
From c5a61ea577f63bb0281c24d21aac33230a984a16 Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Fri, 23 May 2025 12:30:00 -0700
Subject: [PATCH 20/24] More
---
content/nginx-one/nginx-configs/_index.md | 4 ++++
content/nginx-one/staged-configs/_index.md | 4 ++++
2 files changed, 8 insertions(+)
diff --git a/content/nginx-one/nginx-configs/_index.md b/content/nginx-one/nginx-configs/_index.md
index 5cf29aa32..1e0f420e0 100644
--- a/content/nginx-one/nginx-configs/_index.md
+++ b/content/nginx-one/nginx-configs/_index.md
@@ -5,6 +5,7 @@ description:
<<<<<<< HEAD
<<<<<<< HEAD
<<<<<<< HEAD
+<<<<<<< HEAD
title: Manage your NGINX instances
=======
title: Organize your NGINX instances
@@ -21,6 +22,9 @@ title: Manage your NGINX instances
=======
title: Add and manage your NGINX instances
>>>>>>> f6a622d3 (More)
+=======
+title: Add and manage NGINX instances
+>>>>>>> 2fec8a44 (More)
weight: 300
url: /nginx-one/nginx-configs
---
diff --git a/content/nginx-one/staged-configs/_index.md b/content/nginx-one/staged-configs/_index.md
index 848874c60..3da38e3e6 100644
--- a/content/nginx-one/staged-configs/_index.md
+++ b/content/nginx-one/staged-configs/_index.md
@@ -3,6 +3,7 @@ description:
<<<<<<< HEAD
<<<<<<< HEAD
<<<<<<< HEAD
+<<<<<<< HEAD
title: Draft new configurations
weight: 400
url: /nginx-one/staged-configs
@@ -14,6 +15,9 @@ title: Draft new instances
=======
title: Draft new instances (Staged Configuration)
>>>>>>> 4da8aa7e (based on Jason's feedback)
+=======
+title: Draft new instances (Staged Configs)
+>>>>>>> 2fec8a44 (More)
weight: 200
url: /nginx-one/how-to/staged-configs
>>>>>>> c7ce27ce (Draft: new N1C doc homepage)
From f2e708f443bf03bba03aa56d20b914fc76752d15 Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Tue, 20 May 2025 11:46:34 -0700
Subject: [PATCH 21/24] Feature: secure your fleet
---
content/nginx-one/getting-started.md | 11 +++++++++++
1 file changed, 11 insertions(+)
diff --git a/content/nginx-one/getting-started.md b/content/nginx-one/getting-started.md
index 6a761fa2f..162dd363f 100644
--- a/content/nginx-one/getting-started.md
+++ b/content/nginx-one/getting-started.md
@@ -9,6 +9,17 @@ docs: DOCS-1393
This guide provides step-by-step instructions on how to activate and start using F5 NGINX One Console. NGINX One is a management console for monitoring and managing NGINX data plane instances.
+## Confirm access to the F5 Distributed Cloud
+
+You can access NGINX One Console through the F5 Distributed Cloud.
+
+1. Log in to [MyF5](https://my.f5.com/manage/s/).
+1. Go to **My Products & Plans > Subscriptions** to see your active subscriptions.
+1. Within one of your subscriptions, you should see either an NGINX and/or a Distributed Cloud subscription
+ - If the above does not appear in any of your subscriptions, please reach out to either your F5 Account Team or Customer Success Manager.
+
+Now identify your tenant. You or someone in your organization should have received an email from no-reply@cloud.f5.com asking you to update your password. The account name referenced in the E-Mail is the tenant name. Navigate to https://YOUR_TENANT_NAME.console.ves.volterra.io to access the F5 Distributed Cloud.
+
## Enable the NGINX One service {#enable-nginx-one}
To get started using NGINX One, enable the service on F5 Distributed Cloud.
From a8a00c06925681bd16aae55d99e8856c7bdf24a1 Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Thu, 22 May 2025 10:45:53 -0700
Subject: [PATCH 22/24] More
---
content/nginx-one/secure-your-fleet/_index.md | 6 ++++++
1 file changed, 6 insertions(+)
create mode 100644 content/nginx-one/secure-your-fleet/_index.md
diff --git a/content/nginx-one/secure-your-fleet/_index.md b/content/nginx-one/secure-your-fleet/_index.md
new file mode 100644
index 000000000..c35f4beab
--- /dev/null
+++ b/content/nginx-one/secure-your-fleet/_index.md
@@ -0,0 +1,6 @@
+---
+title: Secure your fleet
+description:
+weight: 350
+url: /nginx-one/secure-your-fleet
+---
From 62df7d8114f9353cbcbe16d1c306ae71aeb5665c Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Fri, 23 May 2025 13:37:45 -0700
Subject: [PATCH 23/24] More
---
content/nginx-one/secure-your-fleet/_index.md | 2 +-
content/nginx-one/secure-your-fleet/secure.md | 53 +++++++++++++++++++
2 files changed, 54 insertions(+), 1 deletion(-)
create mode 100644 content/nginx-one/secure-your-fleet/secure.md
diff --git a/content/nginx-one/secure-your-fleet/_index.md b/content/nginx-one/secure-your-fleet/_index.md
index c35f4beab..d9fea82ff 100644
--- a/content/nginx-one/secure-your-fleet/_index.md
+++ b/content/nginx-one/secure-your-fleet/_index.md
@@ -1,6 +1,6 @@
---
title: Secure your fleet
description:
-weight: 350
+weight: 450
url: /nginx-one/secure-your-fleet
---
diff --git a/content/nginx-one/secure-your-fleet/secure.md b/content/nginx-one/secure-your-fleet/secure.md
new file mode 100644
index 000000000..cca84bf13
--- /dev/null
+++ b/content/nginx-one/secure-your-fleet/secure.md
@@ -0,0 +1,53 @@
+---
+title: "Set up security alerts"
+weight: 500
+toc: true
+type: how-to
+product: NGINX One
+docs: DOCS-000
+---
+
+The F5 Distributed Cloud generates alerts from all its services including NGINX One. You can configure rules to send those alerts to a receiver of your choice. These instructions walk you through how to configure an email notification when we see new CVEs or detect security issues with your NGiNX instances.
+
+This page describes basic steps to set up an email alert. For authoritative documentation, see
+[Alerts - Email & SMS](https://flatrender.tora.reviews/docs-v2/shared-configuration/how-tos/alerting/alerts-email-sms).
+
+## Configure alerts to be sent to your email
+
+To configure security-related alerts, follow these steps:
+
+1. Navigate to the F5 Distributed Cloud Console at https://INSERT_YOUR_TENANT_NAME.console.ves.volterra.io.
+1. Find **Audit Logs & Alerts** > **Alerts Management**
+1. Select **Add Alert Receiver**
+1. Configure the **Alert Receivers**
+ 1. Enter the name of your choice
+ 1. (Optional) Specify a label and description
+1. Under **Receiver**, select Email and enter your email address.
+1. Select **Save and Exit**.
+1. Your Email receiver should now appear on the list of Alert Receivers.
+1. Under the Actions column, select Verify Email.
+1. Select **Send email** to confirm
+1. You should receive a verification code in the email provided. Copy that code.
+1. Under the Actions column, select **Enter verification code**.
+1. Paste the code and select **Verify receiver**.
+
+## Configure Alert Policy
+
+Next, configure the policy that identifies when you'll get an alert.
+
+1. Navigate to **Alerts Management > Alert Policiei**.
+1. Select Add Alert Policy.
+ 1. Enter the name of your choice
+ 1. (Optional) Specify a label and description
+1. Under Alert Reciever Configuration > Alert Receivers, select the Alert Receiver you just created
+1. Under Policy Rules select Configure.
+1. Select Add Item.
+1. Under Select Alerts (TBD)
+1. Set the Action as Send and select Apply
+
+Now set a second alert related to Common Vulnerabilities and Exposures (CVEs).
+
+1. Select Add Item.
+1. Under Select Alerts {adding additional Alert type for CVE).
+1. Set the Action as Send and select Apply.
+1. Select **Save and Exit**.
From e7d69aa459acacd1a2cb58ac693d300cd5657904 Mon Sep 17 00:00:00 2001
From: Mike Jang <3287976+mjang@users.noreply.github.com>
Date: Tue, 27 May 2025 08:12:42 -0700
Subject: [PATCH 24/24] Apply suggestions from code review
Co-authored-by: yar
---
content/nginx-one/secure-your-fleet/secure.md | 12 ++++++------
1 file changed, 6 insertions(+), 6 deletions(-)
diff --git a/content/nginx-one/secure-your-fleet/secure.md b/content/nginx-one/secure-your-fleet/secure.md
index cca84bf13..638874258 100644
--- a/content/nginx-one/secure-your-fleet/secure.md
+++ b/content/nginx-one/secure-your-fleet/secure.md
@@ -7,7 +7,7 @@ product: NGINX One
docs: DOCS-000
---
-The F5 Distributed Cloud generates alerts from all its services including NGINX One. You can configure rules to send those alerts to a receiver of your choice. These instructions walk you through how to configure an email notification when we see new CVEs or detect security issues with your NGiNX instances.
+The F5 Distributed Cloud generates alerts from all its services including NGINX One. You can configure rules to send those alerts to a receiver of your choice. These instructions walk you through how to configure an email notification when we see new CVEs or detect security issues with your NGINX instances.
This page describes basic steps to set up an email alert. For authoritative documentation, see
[Alerts - Email & SMS](https://flatrender.tora.reviews/docs-v2/shared-configuration/how-tos/alerting/alerts-email-sms).
@@ -17,8 +17,8 @@ This page describes basic steps to set up an email alert. For authoritative docu
To configure security-related alerts, follow these steps:
1. Navigate to the F5 Distributed Cloud Console at https://INSERT_YOUR_TENANT_NAME.console.ves.volterra.io.
-1. Find **Audit Logs & Alerts** > **Alerts Management**
-1. Select **Add Alert Receiver**
+1. Find **Audit Logs & Alerts** > **Alerts Management**.
+1. Select **Add Alert Receiver**.
1. Configure the **Alert Receivers**
1. Enter the name of your choice
1. (Optional) Specify a label and description
@@ -26,7 +26,7 @@ To configure security-related alerts, follow these steps:
1. Select **Save and Exit**.
1. Your Email receiver should now appear on the list of Alert Receivers.
1. Under the Actions column, select Verify Email.
-1. Select **Send email** to confirm
+1. Select **Send email** to confirm.
1. You should receive a verification code in the email provided. Copy that code.
1. Under the Actions column, select **Enter verification code**.
1. Paste the code and select **Verify receiver**.
@@ -35,8 +35,8 @@ To configure security-related alerts, follow these steps:
Next, configure the policy that identifies when you'll get an alert.
-1. Navigate to **Alerts Management > Alert Policiei**.
-1. Select Add Alert Policy.
+1. Navigate to **Alerts Management > Alert Policies**.
+1. Select **Add Alert Policy**.
1. Enter the name of your choice
1. (Optional) Specify a label and description
1. Under Alert Reciever Configuration > Alert Receivers, select the Alert Receiver you just created
{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Get started")}}
See benefits from the NGINX One Console
{{ end }} +<<<<<<< HEAD {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Draft new configurations")}}Work with Staged Configurations
+======= + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Set up new instances")}} +Collaborate with Staged Configurations
+ {{ end }} + {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Secure your fleet")}} +Configure alerts that match your security policies
+>>>>>>> 3dbfb304 (Sync with presentation) {{ end }} <<<<<<< HEAD +>>>>>>> 42d749df (Make more prod ready) {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Watch your NGINX instances")}}Keep an inventory of your deployments
>>>>>>> 09d8a53f (More) From 7254b72c81a96fd5657e9aa29d1c97de72a2c4cd Mon Sep 17 00:00:00 2001 From: Mike Jang <3287976+mjang@users.noreply.github.com> Date: Thu, 22 May 2025 11:15:19 -0700 Subject: [PATCH 16/24] More --- .../includes/nginx-one/how-to/add-instance.md | 3 ++ .../nginx-one/nginx-configs/add-instance.md | 30 +++---------- layouts/partials/list-main.html | 43 +------------------ 3 files changed, 10 insertions(+), 66 deletions(-) diff --git a/content/includes/nginx-one/how-to/add-instance.md b/content/includes/nginx-one/how-to/add-instance.md index 94f0b628b..b9c5c86b8 100644 --- a/content/includes/nginx-one/how-to/add-instance.md +++ b/content/includes/nginx-one/how-to/add-instance.md @@ -1,8 +1,11 @@ --- docs: +<<<<<<< HEAD files: - content/nginx-one/connect-instances/add-instance.md - content/nginx-one/getting-started.md +======= +>>>>>>> 4067237f (More) --- You can add an instance to NGINX One Console in the following ways: diff --git a/content/nginx-one/nginx-configs/add-instance.md b/content/nginx-one/nginx-configs/add-instance.md index ddf5eb095..fd3b70fd5 100644 --- a/content/nginx-one/nginx-configs/add-instance.md +++ b/content/nginx-one/nginx-configs/add-instance.md @@ -16,34 +16,16 @@ to set up a data plane key to connect your instances to NGINX One. Before you add an instance to NGINX One Console, ensure: -- You have administrator access to NGINX One Console. -- You have configured instances of NGINX that you want to manage through NGINX One Console. -- You have or are ready to configure a data plane key. -- You have or are ready to set up managed certificates. +- You have [administrator access]({{< ref "/nginx-one/rbac/roles.md" >}}) to NGINX One Console. +- You have [configured instances of NGINX]({{< ref "/nginx-one/getting-started.md#add-your-nginx-instances-to-nginx-one" >}}) that you want to manage through NGINX One Console. +- You have or are ready to configure a [data plane key]({{< ref "/nginx-one/getting-started.md#generate-data-plane-key" >}}). +- You have or are ready to set up [managed certificates]({{< ref "/nginx-one/certificates/manage-certificates.md" >}}). {{< note >}}If this is the first time an instance is being added to a Config Sync Group, and you have not yet defined the configuration for that Config Sync Group, that instance provides the template for that group. For more information, see [Configuration management]({{< ref "nginx-one/config-sync-groups/manage-config-sync-groups#configuration-management" >}}).{{< /note >}} ## Add an instance -You can add an instance to NGINX One Console in the following ways: - -- Directly, under **Instances** -- Indirectly, by selecting a Config Sync Group, and selecting **Add Instance to Config Sync Group** - -In either case, NGINX One Console gives you a choice for data plane keys: - -- Create a new key -- Use an existing key - -NGINX One Console takes the option you use, and adds the data plane key to a command that you'd use to register your target instance. You should see the command in the **Add Instance** screen in the console. - -Connect to the host where your NGINX instance is running. Run the provided command to [install NGINX Agent]({{< ref "/nginx-one/getting-started#install-nginx-agent" >}}) dependencies and packages on that host. - -```bash -curl https://agent.connect.nginx.com/nginx-agent/install | DATA_PLANE_KEY="{{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Get started")}}
See benefits from the NGINX One Console
{{ end }} -<<<<<<< HEAD {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Draft new configurations")}}Work with Staged Configurations
-======= - {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Set up new instances")}} -Collaborate with Staged Configurations
{{ end }} - {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Manage your NGINX instances")}}Monitor and maintain your deployments
-======= -======= - {{ end }} --> ->>>>>>> 42d749df (Make more prod ready) - {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Watch your NGINX instances")}} -Keep an inventory of your deployments
->>>>>>> 09d8a53f (More) {{ end }} -<<<<<<< HEAD {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Organize users with RBAC")}}Assign responsibilities with role-based access control
-======= - {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Monitor your certificates")}} -<<<<<<< HEAD -Detect and resolve expired SSL certs in minutes
->>>>>>> 5e6d32b4 (new messages) -======= -Update your SSL certs before they expire
->>>>>>> 3dbfb304 (Sync with presentation) {{ end }} -<<<<<<< HEAD {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Automate with the NGINX One API")}}Manage your NGINX fleet over REST
-======= - {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Organize your administrators with RBAC")}} -Secure your systems with role-based access control
- {{ end }} - {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Change multiple instances with one push")}} -Simplify changes with Config Sync Groups
- {{ end }} - {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "NGINX One API")}} -<<<<<<< HEAD -Automate NGINX fleet management
->>>>>>> 09d8a53f (More) -======= -Automate NGINX fleet management from the CLI
->>>>>>> 5e6d32b4 (new messages) {{ end }} {{ if and (eq $PageTitle "F5 NGINX One Console") (eq .Title "Glossary")}}Learn terms unique to NGINX One Console
From 245683258ebeeb4f14be9808f0c6045c00277da0 Mon Sep 17 00:00:00 2001 From: Mike Jang <3287976+mjang@users.noreply.github.com> Date: Thu, 22 May 2025 11:48:39 -0700 Subject: [PATCH 17/24] more --- content/nginx-one/api/_index.md | 4 + content/nginx-one/nginx-configs/_index.md | 4 + .../manage-config-sync-groups.md | 239 ------------------ content/nginx-one/staged-configs/_index.md | 4 + 4 files changed, 12 insertions(+), 239 deletions(-) delete mode 100644 content/nginx-one/nginx-configs/manage-config-sync-groups.md diff --git a/content/nginx-one/api/_index.md b/content/nginx-one/api/_index.md index 1735740f8..b74c67e09 100644 --- a/content/nginx-one/api/_index.md +++ b/content/nginx-one/api/_index.md @@ -1,9 +1,13 @@ --- <<<<<<< HEAD +<<<<<<< HEAD title: Automate with the NGINX One API ======= title: NGINX One API >>>>>>> c7ce27ce (Draft: new N1C doc homepage) +======= +title: Automation with the NGINX One API +>>>>>>> 614bafed (more) description: weight: 700 url: /nginx-one/api diff --git a/content/nginx-one/nginx-configs/_index.md b/content/nginx-one/nginx-configs/_index.md index 18ece7e11..4b732ef6e 100644 --- a/content/nginx-one/nginx-configs/_index.md +++ b/content/nginx-one/nginx-configs/_index.md @@ -2,6 +2,7 @@ description: <<<<<<< HEAD <<<<<<< HEAD +<<<<<<< HEAD title: Manage your NGINX instances ======= title: Organize your NGINX instances @@ -9,6 +10,9 @@ title: Organize your NGINX instances ======= title: Watch your NGINX instances >>>>>>> 09d8a53f (More) +======= +title: Access and connect to your NGINX instances +>>>>>>> 614bafed (more) weight: 300 url: /nginx-one/nginx-configs --- diff --git a/content/nginx-one/nginx-configs/manage-config-sync-groups.md b/content/nginx-one/nginx-configs/manage-config-sync-groups.md deleted file mode 100644 index 41589dadd..000000000 --- a/content/nginx-one/nginx-configs/manage-config-sync-groups.md +++ /dev/null @@ -1,239 +0,0 @@ ---- -docs: null -title: Manage config sync groups -toc: true -weight: 300 -type: -- how-to ---- - -## Overview - -This guide explains how to create and manage config sync groups in the F5 NGINX One Console. Config sync groups synchronize NGINX configurations across multiple NGINX instances, ensuring consistency and ease of management. - -If you’ve used [instance groups in NGINX Instance Manager]({{< ref "/nim/nginx-instances/manage-instance-groups.md" >}}), you’ll find config sync groups in NGINX One similar, though the steps and terminology differ slightly. - -## Before you start - -Before you create and manage config sync groups, ensure: - -- You have access to the NGINX One Console. -- You have the necessary permissions to create and manage config sync groups. -- NGINX instances are properly registered with NGINX One if you plan to add existing instances to a config sync group. - -## Important considerations - -- **NGINX Agent configuration file location**: When you run the NGINX Agent installation script to register an instance with NGINX One, the script creates the `agent-dynamic.conf` file, which contains settings for the NGINX Agent, including the specified config sync group. This file is typically located in `/var/lib/nginx-agent/` on most systems; however, on FreeBSD, it's located at `/var/db/nginx-agent/`. - -- **Mixing NGINX Open Source and NGINX Plus instances**: You can add both NGINX Open Source and NGINX Plus instances to the same config sync group, but there are limitations. If your configuration includes features exclusive to NGINX Plus, synchronization will fail on NGINX Open Source instances because they don't support these features. NGINX One allows you to mix NGINX instance types for flexibility, but it’s important to ensure that the configurations you're applying are compatible with all instances in the group. - -- **Single config sync group membership**: An instance can join only one config sync group at a time. - -- **Configuration inheritance**: If the config sync group already has a configuration defined, that configuration will be pushed to instances when they join. - -- **Using an instance's configuration for the group configuration**: If an instance is the first to join a config sync group and the group's configuration hasn't been defined, the instance’s configuration will become the group’s configuration. Any instances added later will automatically inherit this configuration. - - {{< note >}} If you add multiple instances to a single config sync group, simultaneously (with automation), follow these steps. Your instances will inherit your desired configuration: - - 1. Create a config sync group. - 1. Add a configuration to the config sync group, so all instances inherit it. - 1. Add the instances in a separate operation. - - Your instances should synchronize with your desired configuration within 30 seconds. {{< /note >}} - -- **Persistence of a config sync group's configuration**: The configuration for a config sync group persists until you delete the group. Even if you remove all instances, the group's configuration stays intact. Any new instances that join later will automatically inherit this configuration. - -- **Config sync groups vs. cluster syncing**: Config sync groups are not the same as cluster syncing. Config sync groups let you to manage and synchronize configurations across multiple NGINX instances as a single entity. This is particularly useful when your NGINX instances are load-balanced by an external load balancer, as it ensures consistency across all instances. In contrast, cluster syncing, like [zone syncing]({{< ref "nginx/admin-guide/high-availability/zone_sync_details.md" >}}), ensures data consistency and high availability across NGINX instances in a cluster. While config sync groups focus on configuration management, cluster syncing supports failover and data consistency. - -## Create a config sync group - -Creating a config sync group allows you to manage the configurations of multiple NGINX instances as a single entity. - -1. On the left menu, select **Config Sync Groups**. -2. Select **Add Config Sync Group**. -3. In the **Name** field, type a name for your config sync group. -4. Select **Create** to add the config sync group. - -## Manage config sync group membership - -### Add an existing instance to a config sync group {#add-an-existing-instance-to-a-config-sync-group} - -You can add existing NGINX instances that are already registered with NGINX One to a config sync group. - -1. Open a command-line terminal on the NGINX instance. -2. Open the `/var/lib/nginx-agent/agent-dynamic.conf` file in a text editor. -3. At the end of the file, add a new line beginning with `instance_group:`, followed by the config sync group name. - - ``` text - instance_group: