Google Cloud Build 2nd Gen connections allow you to connect to GitHub, GitHub Enterprise, and GitLab (including Self Hosted).
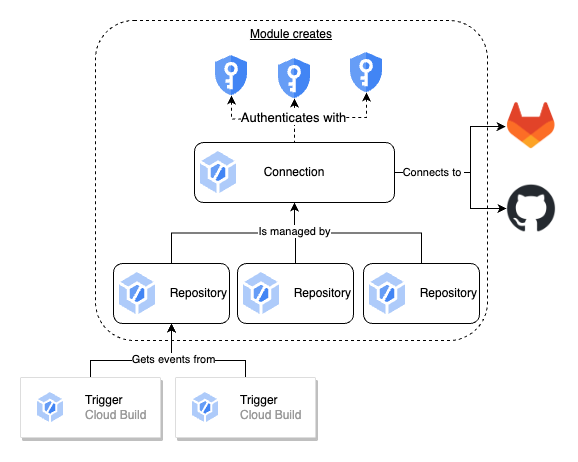
This module creates the secrets as well as the required IAM to allow the Cloud Build Service Agent to access the secrets and set up the connection to the chosen host. Additionally, you are able to associate one or more repositories with the created connection.
The diagram below shows how the different components of Cloud Build 2nd Gen work together and which are provided by this module
Add the module code with required inputs for the Git Provider you are using. Note that a different set of inputs are required for different providers. The first time you instantiate the module the input create_connection should be false or not provided, this is because there is a dependency on the secret values being added via the Google Cloud Console or gcloud. Once you have added the secret versions, set create_connection to true and the connection as well as related repositories will be created.
For GitHub Enterprise and GitLab Enterprise Edition hosted in a private network there is additional documentation for GitHub and GitLab. More specific Service directory documentation also exists.
Each Git provider has different requirements to create the connection. Review the Google documentation to see what settings are required for each provider ahead of creating the module.
| Name | Description | Git Provider | Type | Default | Required |
|---|---|---|---|---|---|
| app_id | Unique identifier for the GitHub Enterprise Application for Cloud Build | ghe | number |
null |
no |
| app_slug | URL friendly name of the GitHub Enterprise application | ghe | string |
null |
no |
| connection_name | Name of the Cloud Build connection | All | string |
n/a | yes |
| create_connection | Create the connection resource only after the secrets have been correctly set. | All | bool |
false |
no |
| git_provider | Which git provider you are connecting to. Options are: gitlab, github, ghe | All | string |
n/a | yes |
| git_url | The Host URI of the Git Server you are connecting to | GitLab, GHE | string |
null |
no |
| installation_id | Unique Identifier for the installation of the Cloud Build application in your Organisation (One application can have many installations) | ghe | number |
null |
no |
| labels | List of labels to apply to the Secret resources | All | map(string) |
null |
no |
| project_id | The project to create resources in. Defaults to provider project | All | string |
null |
no |
| repositories | List of repositories to create connection to as name = value pair. Defaults to creating none | All | map(string) |
{} |
no |
| service_name | Service Directory name in format: projects/{project}/locations/{location}/namespaces/{namespace}/services/{service}. |
GitLab, GHE | string |
null |
no |
| ssl_ca | SSL certificate to use for requests to GitHub Enterprise/Self-Hosted GitLab | GitLab, GHE | string |
null |
no |
The location of the Secrets created for the selected Git Provider will be provided. The other Secret IDs will be fixed to null
| Name | Description |
|---|---|
| connection_id | Unique Identifier for the connection in format: projects/{{project}}/locations/{{location}}/connections/{{name}} |
| ghe_private_key_secret_id | Secret ID for GHE Private Key in format: projects/{{project}}/secrets/{{secret_id}} |
| ghe_webhook_secret_id | Secret ID for GHE Webhook in format: projects/{{project}}/secrets/{{secret_id}} |
| github_oauth_secret_id | Secret ID for GitHub Oauth in format: projects/{{project}}/secrets/{{secret_id}} |
| gitlab_authorizer_secret_id | Secret ID for Gitlab Read Write Authorizer in format: projects/{{project}}/secrets/{{secret_id}} |
| gitlab_read_authorizer_secret_id | Secret ID for Gitlab Read Only Authorizer in format: projects/{{project}}/secrets/{{secret_id}} |
| gitlab_webhook_secret_id | Secret ID for Gitlab Webhook in format: projects/{{project}}/secrets/{{secret_id}} |
| repository_ids | Unique identifier for the repository resources managed by the connection. Access via module_name.repository_ids[$var.repositories.key]. In format: projects/{{project}}/locations/{{location}}/connections/{{parent_connection}}/repositories/{{name}} |
module "cloudbuild_v2" {
source = "github.com/kasna-cloud/terraform-google-cloud-build-gen-2"
create_connection = true # set to true once the secrets are added
connection_name = "example"
connection_location = var.region
git_url = "https://gitlab.com"
repositories = {
gitlab = "https://gitlab.com/gitlab-org/gitlab.git"
another = "https://gitlab.com/inkscape/inkscape.git"
}
git_provider = "gitlab"
labels = {
test = "val"
}
}