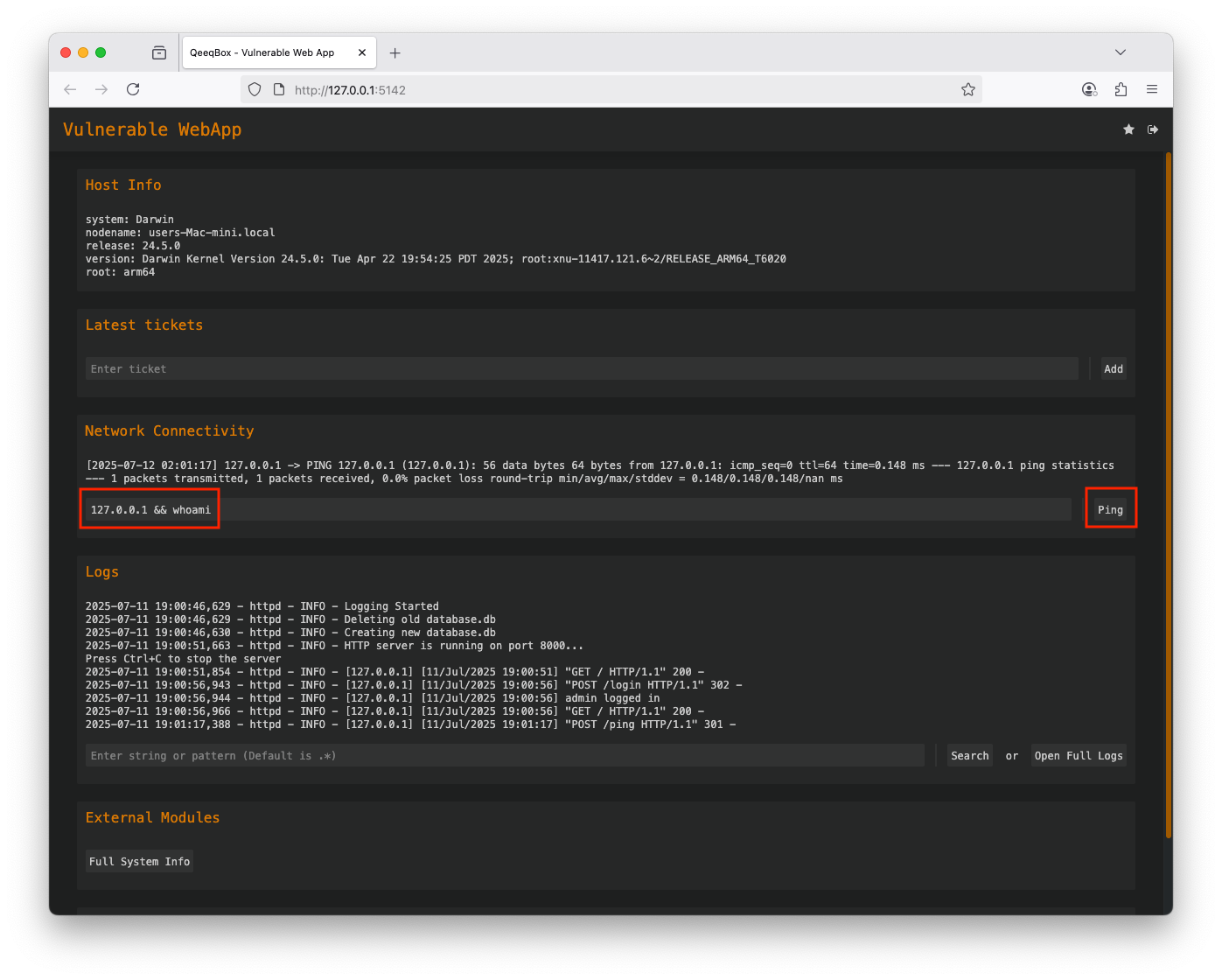
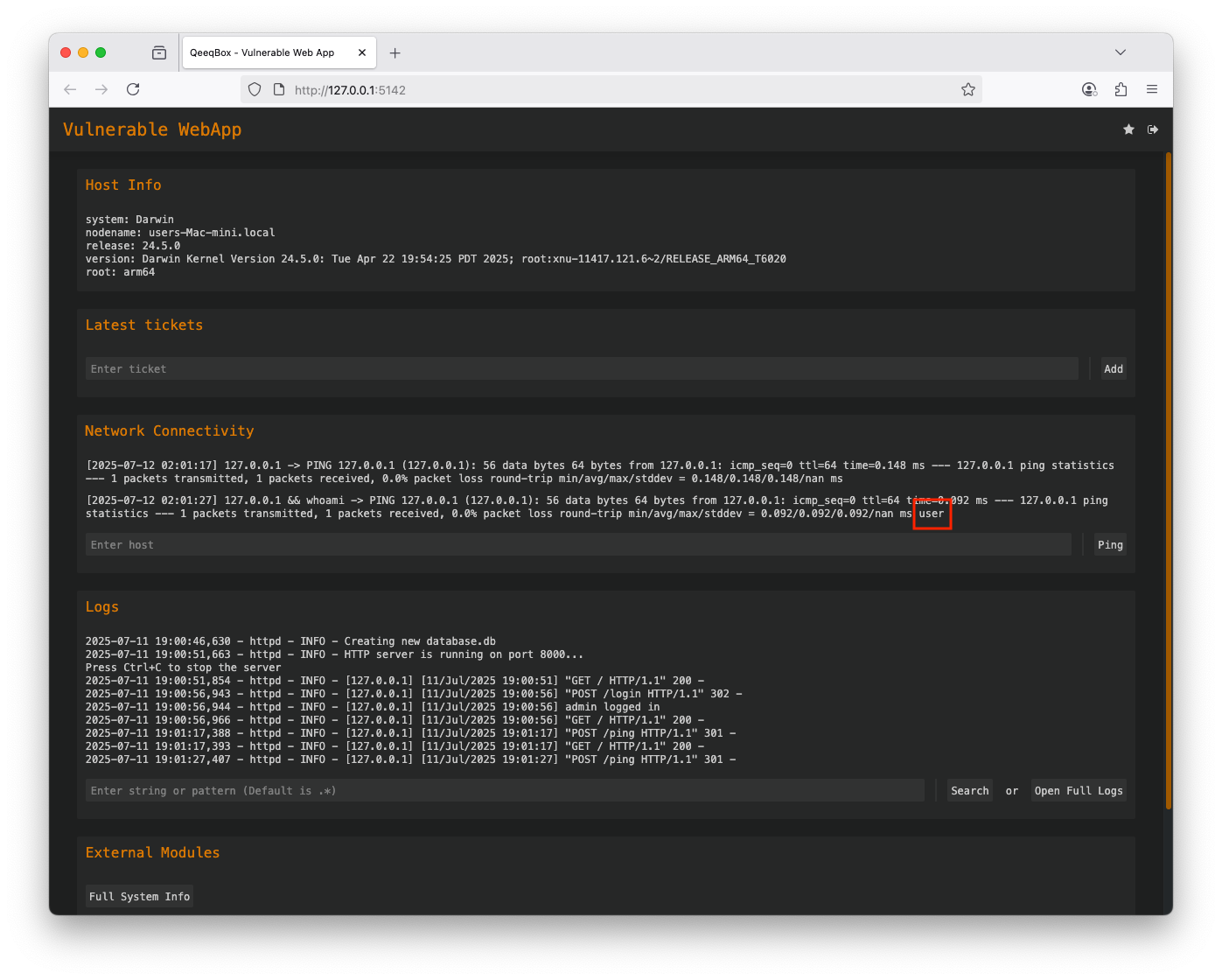
An application utilizes operating system (OS) commands to perform actions. A threat actor can exploit this feature by tricking the application into executing a malicious payload containing OS commands
Clone this current repo recursively
git clone --recursive https://github.com/qeeqbox/os-command-injectionRun the webapp using Python
python3 os-command-injection/vulnerable-web-app/webapp.pyOpen the webapp in your browser 127.0.0.1:5142
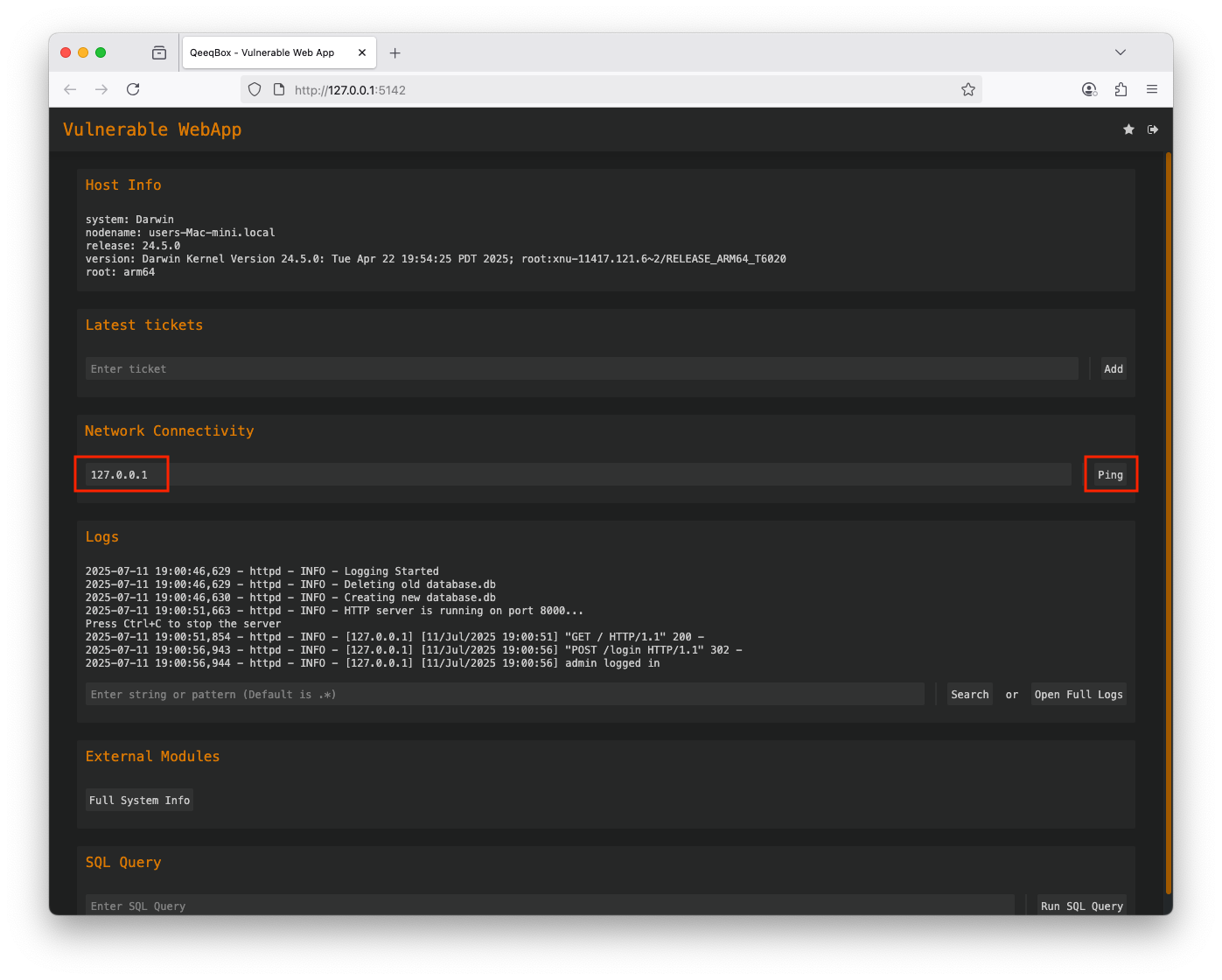
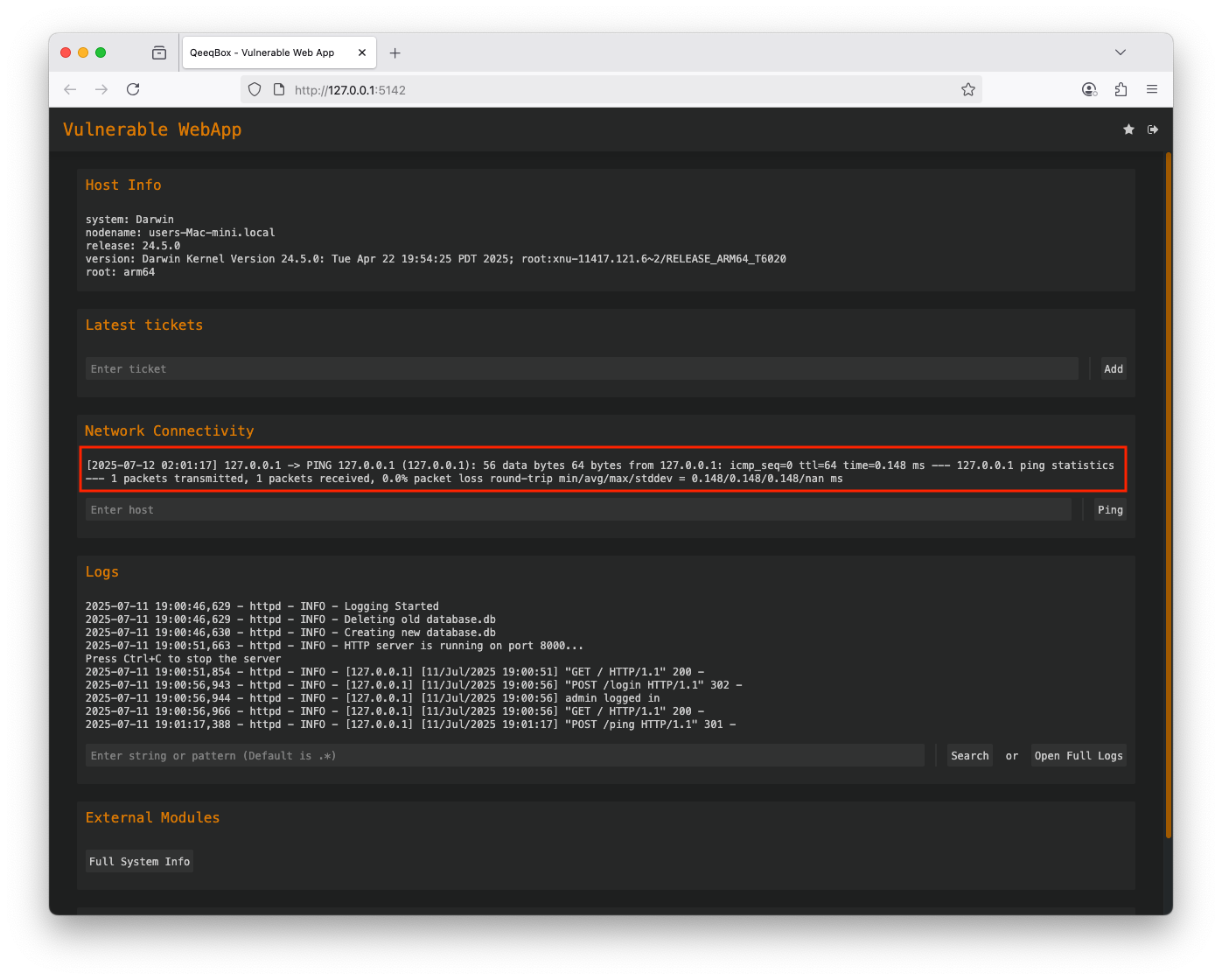
Use the default credentials (username: admin and password: admin) to login The application allows users to check network connectivity using the host's ping OS command, enter 127.0.0.1 The ping OS command is executed A threat actor could use logical opertator (&, &&, | or ||) or commands seperators (;) to make the host run extra commands The host executed the ping command and the whoami commandWhen the user enters a hostname or IP to check their network connectivity, the webapp calls the add_ping() function. This function uses the internal ping OS command, the dynamic value from the user can contain a malicious payload that also gets executed by the host
@logged_in
@check_access(access="ping")
def add_ping(self, ping):
with Popen("ping -c 1 " + ping, stdout=PIPE, stderr=STDOUT, shell=True) as process, connect(DATABASE, isolation_level=None) as connection:
cursor = connection.cursor()
cursor.execute("INSERT into ping(username, ping, output) values(?,?,?)", (self.session["username"], ping, process.communicate()[0].decode("utf-8")))
return True
return FalseCritical
- Session Hijacking
- Credential Theft
- Server input validation
cb251c97-067d-4f13-8195-4f918273f41b